Presentation on "System Software". PC software. Operating system System software operating system presentation
system software (public programs),
performing various auxiliary
functions, such as making copies of the used
information, issuance of reference information about
computer, checking device performance
computer, etc.
application software that provides execution
required work on a PC: editing
text documents, drawing or
pictures, processing of information arrays and
etc.
instrumental software (programming systems),
ensuring the development of new programs for
computer in the programming language.
System software
These are public programs not associated with a specificusing a PC and perform traditional functions:
scheduling and task management, input management
output, etc.
System software includes:
operating systems (this program is loaded into RAM
when you turn on the computer)
shell programs (provide more convenient and
a visual way to communicate with a computer than using
DOS command line like Norton Commander)
operating shells - interface systems that
are used to create graphical interfaces,
multiprogramming, etc. Drivers (programs designed for
control of ports of peripheral devices,
usually loaded into RAM when
start the computer)
utilities (auxiliary or service
programs that present to the user
a number of additional services)
The utilities include:
file managers or file managers
dynamic data compression
(allow to increase the amount of information by
disk due to its dynamic compression) viewers and playback tools
diagnostic tools; controls allow
check your computer configuration and check
the performance of computer devices, before
total hard drives
means of communication (communication
programs) are designed to organize the exchange
information between computers
computer security tools
(backup, anti-virus software).
Application software
Application packages are a systemprograms that by scope
are divided into problem-oriented,
general purpose and integrated packages
packages. Modern integrated
packages contain up to five functional
components: test and table
processor, DBMS, graphics editor,
telecommunication facilities.
Application software
Application software, for example, includes:Office suite MS OFFICE
Accounting systems
Financial analytical systems
Integrated office packages
CAD - systems (automated
design)
HTML or Web Editors
Browsers - Web viewers
Graphic editor
Instrumental software
Tooling software or systemsprogramming are systems for
automation of the development of new programs
in the programming language.
Borland Delphi - designed to solve
practically any task of applied
programming
Microsoft Visual C ++ - This tool allows
develop any applications running in
OS environment such as Microsoft Windows
File systems
All modern operating systems provide creationfile system that is intended for
storage of data on disks and providing
access to them.
The main functions of the file system can be
divided into two groups:
File systems
Functions for working with files (creating,delete, rename files, etc.)
Functions for working with data that
stored in files (write, read, search
data, etc.)
File systems
To the file structure maintenance functioninclude the following operations occurring
operating system:
creating and naming files;
creating directories (folders) and assigning them
names;
renaming files and directories
(folders); copying and moving files
between computer disks and between directories
(folders) of one disk;
File systems
deleting files and directories (folders);navigating the file structure with a target
access to a given file, directory (folder);
file attributes management.
Integrated systems
Integrated packages area set of several software products,
combined into a single convenient tool.
The most advanced ones include
text editor, organizer, electronic
table, DBMS, support tools
email creation program
presentation graphics.
CASE technologies
CASE (Computer-Aided Software)Engineering) - a set of tools and methods
software engineering for design
software that helps
provide high quality programs,
error-free and easy to maintain
software products. Also under CASE
understand the totality of methods and means
information systems design with
using CASE tools.
CASE technologies
Development automation toolsprograms (CASE-tools) - tools
automation of design processes and
software development for
systems analyst, software developer and
programmer
CASE technologies
analysis tools - designed forbuilding and analyzing a subject model
area;
database design tools;
application development tools;
CASE technologies
process reengineering tools(fundamental rethinking and
radical redesign of business processes to maximize
effect of industrial and economic and
financial and economic activities,
formalized by appropriate
organizational and administrative and
regulatory documents. Reengineering
uses specific means
presentation and processing of problematic
information that is understandable to both managers and
information systems developers.);
CASE technologies
planning and management toolsproject;
testing tools;
documentation tools.
Software: system / application System software is a set of control and processing programs, descriptions and instructions that ensure the functioning of a computing system, as well as the development and execution of user programs. Synonym: "special software". Application software is a set of programs for solving specific problems from various fields of computer application. Synonym: "common software".


Operating systems OS / 360, EU OS, RSX, RT11,… Multics, Unix Novell NetWare, IBM OS / 2 CP / M, Q-DOS, MS-DOS,… Microsoft Windows… XP, Vista, Seven,… Unix-like , Linux Apple MacOS…, Tiger, X Leopard,… PalmOS, Symbian,… WindRiver VxWorks,… Ghost, gOS Cloud…

Operating shells MS DOS: Command.com NDOS.com (Norton Utilites for DOS v) OS / 2: Workplase Shell Windows: Windows GUI Linux: Bourne Again Shell (BASH) TCSH – shell ...

DOS, Windows and other OSSiOs produced by Microsoft Operating shells launched from DOSDOS –Windows 1.0 | Windows 2.x | Windows 3.xWindows 1.0Windows 2.xWindows 3.x OS Family Windows 9x –Windows 95 | Windows 98 | Windows MeWindows 95Windows 98Windows Me Windows NT –NT 3.1 Family | NT 3.5 | NT 3.51 | NT 4.0 | 2000 (NT 5.0) | XP (NT 5.1) | Server 2003 (NT 5.2) | FLP | Vista (NT 6.0) | Home Server | Server 2008NT 3.1NT 3.5NT 3.51NT XPServer 2003FLPVistaHome ServerServer 2008 Windows CE –CE 2.0 OS Family | CE 3.0 | CE 4.0 | CE 5.0 | CE 6.0 | MobileCE 2.0CE 3.0CE 4.0CE 5.0CE 6.0 Mobile Under development –Seven (Vienna / Blackcomb; NT 7.0) Seven Closed –Neptune | Nashville | OdysseyNeptuneNashvilleOdyssey More projects –Xenix | MS-DOS | OS / 2 | Cairo | SingularityXenixMS-DOSOS / 2CairoSingularity

Linux distributions… Slackware S.U.S.E Suse / OpenSUSE… Gentoo Fregate… Red Hat / Fedora Core Mandrake Mandriva… ASPLinux… Debian GNU / Linux Corel Linux Xandros… Mepis… Lindows Linspire… LiveCD Knoppix Gnoppix, Kurumin… Ubuntu Kubuntu, Edubuntu,……

Mobile OSs EPOC32 (Psion, 1990s) Symbian: - UIQ platform Up to version 3.0 (Sony Ericsson) Versions 3.1, 3.2 (Motorola since 2007) - S60 platform (from Nokia Series 60, 2001) Revision 3 Revision 5 (draft, for Nokia Tube ) Pocket PC Windows Mobile v.6.0 / 6.1 –Standard –Professional (sensor) OS X iPhone (for iPhone, iPhone 3G, iPod Touch) Linux –MobiLinux –Google Android (for HTC Dream)

Specialized real-time operating systems: OS for automotive electronics, etc. Facts: An average car has about 70 microprocessors installed Engine management system alone - several million lines of code ... Projects: JasPar (Japan Automotive Software Platform and Architecture: Toyota, Honda, Nissan, ...) Toyota + Nagoya University OSEK (Bosh + BMW, DaimlerChrysler) Microsoft SyncOS (Windows Auto) Wind River VVxWorks GHS Integrity ...




OS classifications By the number of users –Single-user (MS-DOS, NetWare, Windows, ...) –Multi-user (UNIX, ...) By access modes –Batch (OS / 360,…) –Interactive (Windows, UNIX,…) –Real time ( QNX, RSX, ...) By the number of tasks being solved –Single-tasking (MS-DOS,…) –Multi-tasking (Windows, UNIX,…) By bit depth (8,16,32,64,…) ...


What is an OS structurally? Option 1. This is the core (minimalist point of view) Option 2. This is the core plus the infrastructure that builds on it: a set of system utilities and user applications, as well as tools for managing them (maximalist point of view) Option 3. This is the core and a set of tools that ensure its functionality ( intermediate point of view)

(Modular) OS structure Kernel Startup utilities (means of loading a kernel image, managing plug-ins and initializing the system) Support utilities (means of providing basic kernel functionality) User utilities System libraries

OS kernel and its functions The core provides interaction of system and user programs with computer hardware: - Allocation of processor time between simultaneously running tasks - Working with physical and virtual memory - Access to data at the file system level, I / O control - Support for network protocols and devices - ...

Software (software, software) - a set of programs executed by a computer system. Software is an integral part of a computer system. It is a logical continuation of technical means. The scope of application of a particular computer is determined by the software created for it. The computer itself has no knowledge of any application. All this knowledge is concentrated in programs running on computers. Software (software, software) - a set of programs executed by a computer system. Software is an integral part of a computer system. It is a logical continuation of technical means. The scope of application of a particular computer is determined by the software created for it. The computer itself has no knowledge of any application. All this knowledge is concentrated in programs running on computers.
All programs running on a computer can be conditionally divided into three types: application programs that directly ensure the performance of the work required by users; application programs system programs designed to control the operation of a computing system, perform various auxiliary functions, for example: system programs to manage computer resources; making copies of the information used; checking the performance of computer devices; issuance of reference information about the computer, etc.; instrumental software systems that facilitate the process of creating new programs for a computer. instrumental software systems


An application program is any specific program that facilitates the solution of a problem within a given problem area. In contrast, the operating system or tooling software does not directly contribute to meeting the end user needs. Application programs can be used either autonomously, that is, to solve the assigned task without the help of other programs, or as part of software systems or packages.


Document editors are the most widely used type of application software. They allow you to prepare documents much faster and more conveniently than using a typewriter. Text editors can provide a variety of functions, namely: Table processors. Table processors are a convenient tool for performing accounting and statistical calculations. Each package contains hundreds of built-in math functions and statistical data processing algorithms. In addition, there are powerful tools for linking tables to each other, creating and editing electronic databases. Computer-aided design (CAD) or CAD (Computer-Aided Design) software package designed to create drawings, design and / or technological documentation and / or 3D models. Among the systems of small and middle class in the world the most popular system is AutoCad from AutoDesk. Domestic package with similar functions - Compass

Graphic editors allow you to create and edit drawings. The simplest editors provide the ability to draw lines, curves, paint areas of the screen, create inscriptions in various fonts, etc. Most editors allow you to process images taken with scanners. Representatives of graphic editors are Adobe Photoshop, Corel Draw. Database management systems (DBMS) allow you to manage large information arrays - databases. Software systems of this type allow you to process arrays of information on a computer, provide input, search, sorting, selection of records, drawing up reports, etc. Representatives of this class of programs are Microsoft Access, Clipper, Paradox, FoxPro. Integrated systems combine the capabilities of a database management system, spreadsheet processor, word processor, business graphics system, and sometimes other capabilities. As a rule, all components of an integrated system have a similar interface, which makes it easier to learn how to work with them. Representatives of integrated systems are Microsoft Office and its free counterpart Open Office.

System programs run together with application programs and are used to manage computer resources by the central processor, memory, and input-output. These are programs of general use that are intended for all computer users. System software is designed so that a computer can efficiently execute application programs.

System software can be divided into: Base software - the minimum set of software tools to ensure the operation of a computer. The basic software includes: operating system; operating shells (text and graphical); network operating system. Service software programs and software complexes that expand the capabilities of the basic software and organize a more convenient environment for the user - utilities.

An operating system is a complex of interconnected system programs, the purpose of which is to organize the user's interaction with a computer and the execution of all other programs. The operating system can be called a software continuation of the computer control device. The operating system hides from the user complex unnecessary details of interaction with the hardware, forming a layer between them. As a result, people are freed from the very time-consuming work of organizing interaction with computer hardware. In addition, it is the OS that provides the ability to customize the computer: the OS determines from which components the computer on which it is installed is assembled, and configures itself to work with these components. Shells are programs designed to make it easier to work with complex software systems such as DOS. They transform the awkward command user interface into a friendly graphical or "menu" interface. Shells provide the user with convenient access to files and extensive services. Network operating systems are a set of programs that provide processing, transmission and storage of data in the network. The network operating system provides users with various types of network services (file management, e-mail, network management processes, etc.), and supports work in subscriber systems.

Utilities (lat. Utilitas benefit) - either expand and supplement the corresponding capabilities of the operating system, or solve independent important tasks. We will briefly describe some types of utilities: programs for monitoring, testing and diagnostics programs-packers (archivers) programs-drivers anti-virus programs programs for creating backup copies of information programs for managing memory programs for optimizing and monitoring the quality of disk space; programs for optimizing and monitoring the quality of disk space; communication programs, etc.

Control, testing and diagnostic programs that are used to check the correct functioning of computer devices and to detect malfunctions during operation; indicate the cause and location of the malfunction; driver programs that expand the capabilities of the operating system to manage input-output devices, RAM, etc .; with the help of drivers, it is possible to connect new devices to the computer or non-standard use of existing ones; Packing programs (archivers) that allow using special algorithms to compress information on disks, i.e. create smaller copies of files, and merge copies of multiple files into one archive file. The use of archiving programs is very useful when creating an archive of files, since in most cases it is much more convenient to store them, having previously compressed them with archiving programs. Representatives of these programs are WinRar and WinZip.

Antivirus programs designed to prevent infection with computer viruses and eliminate the consequences of virus infection; Representatives of the antivirus family of programs - Kaspersky Antivirus, DrWeb, Norton Antivirus. programs for creating backup copies of information allow you to periodically copy important information located on the hard disk of your computer to additional media. Backup software representatives - APBackUp, Acronis True Image, disk space optimization and quality control software; communication programs are designed to organize the exchange of information between computers. These programs allow you to conveniently transfer files from one computer to another by connecting a cable to their serial ports. Another type of such programs allows computers to communicate over the telephone network (if a modem is available). They make it possible to send and receive fax messages. Representatives of communication programs - Venta Fax, Cute FTP. memory management programs that provide more flexible use of RAM;

Tools are programs that are used in the development, revision, or development of other application or system programs. Software development tools can provide assistance at all stages of software development. By their purpose they are close to programming systems, programming systems.

A programming system is a system for developing new programs in a specific programming language. Modern programming systems usually provide users with powerful and convenient programming tools. They include: a compiler or interpreter, a compiler or an interpreter, an integrated development environment; tools for creating and editing program texts; extensive libraries of standard programs and functions; debug programs, i.e. programs that help to find and fix errors in the program; powerful graphics libraries; utilities for working with libraries; built-in help service; other specifics.

Translator is a translator program. It converts a program written in one of the high-level languages \u200b\u200binto a program consisting of machine instructions. Translators are implemented as compilers or interpreters. Compiler and interpreter differ significantly in terms of how the work is done. A compiler reads the entire program, translates it and creates a complete version of the program in machine language, which is then executed. The interpreter (English interpreter interpreter, interpreter) translates and executes the program line by line. After the program is compiled, neither the original program nor the compiler is needed anymore. At the same time, the program processed by the interpreter must be re-translated into machine language each time the program is started. Compiled programs run faster, but interpreted programs are easier to fix and change. Popular programming systems - Turbo Basic, Quick Basic, Turbo Pascal, Turbo C. Borland C ++, Borland Delphi, etc.

Most systems today are smoothly flowing to the Web. The World Wide Web is pulling in more and more applications. Databases are acquiring Web-based user interfaces instead of previous desktop applications. Ultimately, it is to be expected that the end user will only need a web browser to be able to meet all possible software needs. In this case, the user does not care which operating system controls the local computer, the main thing is the reliability and performance of the server. (For example, Microsoft Office might be installed on remote servers rather than on end-user systems, but it will launch applications as fast as local PCs.) Thus, all programs will be able to run both locally and remotely via the Web.

Slide 2
Memory organization
The physical memory that the processor has access to via the address bus is called random access memory (or random access memory - RAM). RAM is organized as a sequence of cells - bytes. Each byte has its own unique address (its number), called physical. The range of values \u200b\u200bof physical addresses depends on the width of the processor address bus. For 80486 and Pentium it ranges from 0 to 232 - 1 (4 GB). For PentiumPro / II / III / IV processors, this range is wider - from 0 to 236 - 1 (64 GB). The 8086 had 1 MB of memory with a 20-bit address bus from 0 to 220-1.
Slide 3
The processor hardware supports two models of RAM usage: In a segmented model, contiguous memory areas (segments) are allocated to the program, and the program itself can only access the data that is in these segments. The page model can be viewed as a superstructure over the segmented model. The main application of this model is associated with the organization of virtual memory, which allows the operating system to use a memory space for the operation of programs larger than the amount of physical memory by combining RAM and external memory into a single address space
Slide 4
By the way, another name for a physical address is a linear address. This duality in the name is precisely due to the presence of a page model for organizing RAM. These names are synonymous only when paging address translation is disabled (in real mode, paging is always disabled). In the paging model, linear and physical addresses have different meanings. The memory management mechanism is completely hardware-based and allows to provide: compact storage of addresses in a machine instruction; flexibility of the addressing mechanism; protection of address spaces of tasks in a multitasking system; support for virtual memory;
Slide 5
In the 80x86 family of processors, the choice of memory access method is determined by the processor operating mode. In real mode, the processor can only access the first megabyte of memory, whose addresses range from 00000 to FFFFF in hexadecimal. In this case, the processor operates in a single-program mode (i.e., at a given time, it can execute only one program). However, at the same time, he can interrupt its execution at any time and switch to the procedure for handling the interrupt received from one of the peripheral devices. Any program that the processor is executing at this moment is allowed access without restriction to any memory areas located within the first megabyte: to RAM - for reading and writing, and to ROM, of course, only for reading. The actual operating mode of the processor is used in the MS DOS operating system, as well as in Windows 95 and 98 when booting in the MS DOS emulation mode.
Slide 6
In protected mode, the processor can simultaneously execute multiple programs. In this case, each process (i.e. running program) can be assigned up to 4 GB of RAM. To prevent the mutual influence of running programs on each other, they are allocated isolated areas of memory. Operating systems such as MS Windows and Linux work in protected mode. In virtual addressing mode of the 8086, the latter actually operates in protected mode. For each task, its own virtual machine is created, which is allocated an isolated 1 MB memory area, and the operation of the 80x86 processor in real addressing mode is fully emulated. For example, on Windows 2000 and XP, an 8086 virtual machine is created each time the user starts a command interpreter window (MS DOS session).
Slide 7
Real addressing mode The distinctive features of the physical memory addressing mechanism in real mode are as follows: The range of physical address change is from 0 to 1 MB, since only 20 least significant bits of the address bus are used during addressing The maximum size of memory addressed using 16-bit registers is 64 KB For access to a specific physical address in all available random access memory uses memory segmentation, i.e. splitting the available address space into 64 KB segments and using instead of a physical logical address in the form:, i.e. combinations of segment start address and intra-segment offset 16-bit segment start address is placed in one of six segment registers (CS, DS, ES, SS, FS, or GS) Programs directly operate on only the 16-bit offset specified relative to the segment start
Slide 8
The least significant hexadecimal digit in the address of each segment is zero, i.e. the address of any segment will always be a multiple of 16 bytes. The segment boundaries are located every 16 bytes of physical addresses. Each of these 16-byte chunks is called a paragraph.
Slide 9
The addresses specified in programs in the form "segment-offset" are automatically converted by the processor to 20-bit linear addresses during the execution of the command as follows:
Slide 10
Example: byte specified in segment-offset form: 8000: 0250 in hex transcription. Logical address: 8000: 0250 –––––––––––––––––––––––––––––– Segment: 80000 + Offset: 0250 ––––––– ––––––––––––––––––––––– Physical Address: 80250 In a typical program written for the 80x86 family of processors, there are usually three segments: code, data, and stack. When the program is started, their base segment addresses are loaded into the CS, DS and SS registers, respectively. In the three remaining registers ES, FS and GS, the program can store pointers to additional segments.
Slide 11
The disadvantages of this memory organization: the segments are uncontrolledly allocated from any address multiple of 16 (since the contents of the segment register are shifted by hardware by 4 bits), and, as a result, the program can access any addresses, including those that do not really exist, have a maximum size 64KB segments can be overlapped with other segments
Slide 12
Protected addressing mode When operating in protected mode, each program can be allocated a block of memory up to 4 GB in size, the addresses of which in hexadecimal notation can vary from 00000000 to FFFFFFFF. It is said that the program is allocated a linear address space. In the protected mode, segment registers (CS, DS, SS, ES, FS, GS) do not store 16-bit base segment addresses, but selector pointers to segment descriptors located in one of the system descriptor tables ... From the information in the descriptor, the operating system determines the linear addresses of program segments. There are two flavors of tables: GlobalDescriptorTable (global descriptor table) and LocalDescriptorTables (local descriptor tables).
Slide 13
Segment descriptor selector structure: The descriptor consists of 8 bytes, which include the base segment address, size and other information:
Slide 14
Descriptor 0 is illegal - it can be safely loaded into the segment register to indicate that the segment register is not currently available, but an interrupt is generated when trying to use it. In a typical program written for protected mode, there are usually three segments: code, data, and stack, information about which is stored in the three segment registers listed below. The CS register stores the pointer to the program code segment descriptor The DS register stores the pointer to the program data segment descriptor The SS register stores the pointer to the program stack segment descriptor
Slide 15
The mapping of a selector-offset pair to a physical address is as follows: If paging is disabled (using a bit in the global control register), the linear address is interpreted as a physical address and sent to memory for reading or writing. On the other hand, if paging is available, the linear address is interpreted as a virtual address and mapped to the physical address using the page table.
Slide 16
In protected mode, hardware memory models are supported: FlatModel (flat, solid or linear model) - memory organization in which all segments are mapped to a single area of \u200b\u200blinear addresses. To do this, all segment descriptors point to the same memory segment, which corresponds to the entire 32-bit physical address space of the computer. For a flat model, at least two descriptors must be generated, one for code references and one for data references.
Slide 17
Descriptors are stored in a special system table called the Global Descriptor Table (GDT). For a flat model, each descriptor has a base address of 0. The value of the field defining the segment boundary is multiplied by the processor by the hexadecimal number 1000. Segments can cover the entire 4 GB range of physical addresses, or only those addresses that are mapped to physical memory. If you set the segment boundary to 4 gigabytes, the segmentation mechanism prevents exceptions from being thrown for memory references that cross the segment boundary.
Slide 18
This model makes it possible to exclude the segmentation mechanism from the system architecture, since all memory operations refer to a common memory space. From a programmer's point of view, this model is the easiest to use, since a single 32-bit integer is enough to store the address of any variable or instruction.
Slide 19
MultisegmentedModel Each program has its own segment descriptor table, called a Local Descriptor Table (LDT). In this case, it becomes possible for each process to create its own set of segments that do not overlap with the segments of other processes. As a result, each segment is in an isolated address space.
Slide 20
The figure shows that each entry in the local descriptor table defines a different memory segment. Each segment descriptor indicates its exact length. For example, a segment starting at address 3000 is 2000 bytes long in hex, because the segment boundary descriptor field is 0002 and 0002x1000 \u003d 2000. By analogy, the length of the segment starting at address 8000 is equal to A000. It should be noted that the Flat Model is implemented as a special case of a segmented model, when the program refers to a segment for which the entire linear space is allocated.
Slide 21
Paging This model is a form of memory management for simulating a large non-segmented address space using a portion of disk memory and a fragmented address space. Provides access to data structures that are larger than the size of the available memory, storing them partly in RAM and partly on disk. In this model, the linear address space is divided into blocks of equal size (usually 4 KB), called pages (page).
Slide 22
The figure shows a linear address divided into three fields: Directory, Page and Offset. The Directory field is used as an index in the page directory to locate the pointer to the correct page table.
Slide 23
The Page field is then processed as an index in the page table to find the physical address of the page block. To obtain the physical address of the required byte or word, the last Offset field is added to the page block address. As a result, you can easily make the total amount of RAM used by all programs running on your computer exceed the amount of real memory on your computer. This is why paging memory is very often called virtual memory. The health of the virtual memory system is ensured by a special program that is part of the operating system called the virtual memory manager.
Slide 24
Paging memory is the best solution to the problem of insufficient memory. The fact is that before starting execution, any program must be loaded into RAM, the size of which is always limited (for example, due to the design features of a computer or the price of a memory module). Computer users usually load several programs into memory at once in order to be able to switch between them during their work (for example, switch from one window to another). On the other hand, the amount of disk memory is much larger than the amount of RAM in a computer, and besides, this memory is much cheaper. Therefore, by using disk memory when paging memory, the user gets the impression that he has unlimited RAM. Of course, you have to pay for everything: the speed of access to disk memory is several orders of magnitude lower than to RAM.
Slide 25
When the program is running, the parts of its RAM (or pages) that are not used at the moment can be painlessly saved to disk. It is said that part of the task is swapped out to disk. It makes sense to store only those pages in the computer's RAM that the processor actively accesses, for example, executes some program code. If the processor must access a page of memory that is currently preempted to disk, a system error (or interrupt) occurs due to a pagefault. This error is handled by the operating system's virtual memory manager, which finds a page on disk that contains the required code or data and loads it into a free area of \u200b\u200bRAM.
Slide 26
Closely related to virtual memory is the topic of protection. The Pentium supports four levels of protection, with level 0 being the most privileged and level 3 the least privileged. At every moment of time, a running program is at a certain level. Each segment in the system also has its own level.
Slide 27
Level 0 is the operating system kernel, which handles I / O processing, memory management, and other primary issues. At level 1, a system call handler. User programs at this level can access procedures to make system calls, but only to a specific and protected list of procedures. Level 2 contains library routines, possibly shared by multiple running programs. User programs can call these procedures and read their data, but cannot modify them. Finally, user programs run at level 3, which is the least secure.
View all slides

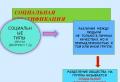
- Software (SW) is a set of special programs that allow organizing information processing using a PC.
- Types of software:
System software
Application software
Programming systems (software tools)
- Since the functioning of a PC is impossible without software, it is an integral part of any computer.

SYSTEM SOFTWARE
System software is a set of programs that ensure the performance of a computer (a set of programs that manage RAM, processor, external devices and files that conduct a dialogue with the user). The main part of the system software is the operating system (OS). The operating system has a lot of work: in order to open any program, it must be found on the hard disk, placed in RAM, having found free space there, "start" the processor to execute the program, control the operation of all devices while the program is running, and in case of failures, carry out diagnostics and display a message for the user.

The most common operating systems are:

SYSTEM SOFTWARE
Interactive mode:
The OS displays a prompt for some action. In response, the user issues a specific command. This can be an operation with files (copy, delete), a command to report the current date or time, etc.
Service programs:
Disk maintenance programs (copying, formatting, "curing", etc.);
Disk compression programs (archivers);
Computer virus fighting programs.

APPLICATION SOFTWARE
Programs with which the user can solve their problems without resorting to programming are called application programs.
All users prefer to have a set of applications that almost everyone needs. They are called GENERAL USE PROGRAMS.
These include:
- These include:
Text and graphic editors (you can write, draw);
Database management systems (DBMS) (various reference books);
Tabular processors allowing calculations;
Communication (network) programs designed to exchange information with other computers connected to a computer network.

APPLICATION SOFTWARE
In addition, there is a large number of special-purpose applications for professional activities. They are often called
PACKAGES OF APPLICATION PROGRAMS.
For example:
Accounting programs,
Computer-aided design systems,
Training programs in various subjects,
Programs for work on various medical
devices (ultrasound, etc.).

Tool software or programming systems (SP)
Systems for developing new programs in a programming language. It is a tool for a programmer's job. Each joint venture is focused on a specific programming language.
There are many programming languages: Pascal, Fortran, C, assembler, etc. In these languages \u200b\u200bthe programmer writes programs, and with the help of programming systems, he brings them into the computer, debugs, tests, and executes.