Use a holographic recording with the fallout 4 virus. Insider information. How a ransomware virus gets on a computer
ClaraOswald 1136726 December 2015 5:08
Locations for research:
- Institute
Your journey to the Institute through the signal interceptor that you built during the Molecular Level story quest is the perfect chance to learn more about the Institute that no one else could find before. So Proctor Ingram gives you a holotape with a virus that can scan their network for information about the Institute.
Insert a holographic recording with a virus into the Institute's terminal
You are required to insert the holotape into any terminal at the Institute. The most convenient way to do this is as soon as you get into the building of the Institute, since right in front of you there will be a free terminal that does not require hacking, and not a single witness is around.

After inserting the holotape into the terminal, start scanning the network. Then don't forget to take the Virus Holotape so you can give it to Proctor Ingram later.
The same holotape with a virus can be given by another faction in similar quests: from the minutemans - "Insider Information" and from the Underground - "Underground undercover." The latter is slightly more complicated than the others, and certainly more secret.
Return the holographic recording to Proctor Ingram
After the task of scanning the network is completed, when convenient, return the holotape with data on the Institute to Proctor Ingram for information analysis. But the opportunity will not appear before you complete the story quest "Closed-type institution", since only after that you can freely move from the Institute and back.
You also have one more task from Elder Maxson, the leader of the Brotherhood of Steel, which must be completed within the walls of the Institute - the quest "From within". Complete for one and him, especially since he is associated with Dr. Lee, whom you will meet while meeting the heads of the Institute.
-1) (_uWnd.alert ("You have already rated this material!", "Error", (w: 270, h: 60, t: 8000)); $ ("# rating_os"). Css ("cursor", "help"). attr ("title", "You have already rated this material"); $ ("# rating_os"). attr ("id", "rating_dis");) else (_uWnd.alert ("Thanks for rating ! "," You did your job ", (w: 270, h: 60, t: 8000)); var rating \u003d parseInt ($ (" # rating_p "). Html ()); rating \u003d rating + 1; $ ("#rating_p"). html (rating); $ ("# rating_os"). css ("cursor", "help"). attr ("title", "You've already rated this stuff"); $ ("# rating_os "). attr (" id "," rating_dis ");)));"\u003e I like 12Information
Why can't everyone coexist peacefully? Unfortunately, in the post-apocalyptic wasteland, resources are limited, and the survival instinct tends to lead to distrust. So choose which faction you want to join and remember, you can always give a holotape from one faction to another faction if you want to switch sides.
As a rule, most penetration tests are carried out according to a fairly simple scheme. First, with the help of social engineering, access to the target environment or its separate link is provided, and then it is infected with technical means. Variations in the conduct of an attack can be different, but usually a classic penetration test is a fusion of technical part and social engineering in very different proportions. The disadvantage of the classic pentest is that you need to "grope" the very employee and then proceed to the next stage. If it was possible to automate the process of finding the weak link and its further exploitation, then this could speed up the process of penetration testing and significantly increase the ultimate chances of success.
WARNING!
All information is provided for informational purposes only. Neither the author nor the editors are responsible for any possible harm caused by the materials of this article.
According to the well-known statistics provided by antivirus companies, about 30% of users do not use antivirus software, they simply disable them or do not update the databases. Based on this, it can be argued that in any average company there is a certain group of people who are very dismissive of information security, and, in turn, it is these people who are advisable to use to carry out an attack. In addition, any functioning system can be influenced by a number of random factors, which can also temporarily paralyze the security system:
- the proxy server settings were out of order, due to which the anti-virus databases were not updated;
- the term of the antivirus license expired, and the management did not take care of its renewal in time;
- a network failure made it impossible to remotely print files, which forced all employees to copy documents to a USB flash drive and print them in another department.
You just need to turn on your imagination, and you can add a dozen more options for the development of events. In summary, it can be argued that in any average organization there are potentially unreliable employees and sometimes circumstances arise that can disrupt the usual work and paralyze protection. Therefore, if you hit in the right place at the right time, the attack will be successful.
In fact, the task boils down to the following: determine that at the moment one of the random events has occurred, which led to a decrease in security, and then use this situation as a disguise and carry out an attack unnoticed.
In fact, the task comes down to finding a person who neglects security, and why not use flash drives for this?
Many virus writers are very fond of flash media, as they allow you to easily and quickly infect computers, and even the most basic USB virus has a good chance of success. The boom of autorun viruses that took place in 2008 is not slowing down five years later; moreover, USB viruses have become even bolder and sometimes do not even hide their presence. And at the same time, an infected flash drive is a universal indicator of the literacy of its owner in the matter of elementary information security. For example, if you collect ten flash drives from different people, then surely three or four of them will have viruses on the flash drives. If a week later you take the flash drives from these people again, then two or three of them will have viruses. Based on this, it can be argued that even the most basic protection is not needed on computers with which they work from this flash drive, or for some reason it is disabled or does not work at all. Thus, even if the most common virus, which is successfully detected by all antiviruses, is distributed only among this group of people, it will be able to infect a large number of computers before being detected. And since these computers do not have protection, then it will also be able to remain operational for a long time.

Implementation
On a specific computer to which flash drives are periodically connected, we install special programworking according to the following algorithm. When connecting another flash drive, the program tries to determine if it is infected. Since it is impossible to take into account all the variety of USB viruses, it makes sense to use a heuristic approach to determine infection based on the following criteria:
- the presence of the autorun.inf file;
- rHS file attributes
- small size of the suspicious file;
- the file system is not NTFS;
- absence of a folder named autorun.inf;
- the presence of shortcut files.
If this flash drive is infected, the program writes it to the database with the serial number and hash of the suspicious file. If after a few days the flash drive is reconnected to this computer (and this happens almost always) and suspicious files still remain on it, then it is infected with our "virus"; if there is no suspicious file left, the program deletes the serial number of this flash drive from the database. When does it become infected new computer, the virus remembers the serial number of the mother's flash drive and never infects or analyzes it, so that after a while it will not give itself out if the owner of the flash drive “grows wiser”.
To get the serial number, let's write the following function based on the GetVolumeInformation API:
String GetFlashSerial (AnsiString DriveLetter) (DWORD NotUsed; DWORD VolumeFlags; char VolumeInfo; DWORD VolumeSerialNumber; GetVolumeInformation (AnsiString (DriveLetter + ": \\\\"). C_str (), NULL, sizeof (VolumeInfo), & VolumeFerialNumber , 0); String S; return S.sprintf ("% X", VolumeSerialNumber);)
It should be noted that the GetFlashSerial function receives not a static unique device identifier, but only the volume serial number. This number is given as a random number and usually changes every time the device is formatted. For our purposes, only the serial number of the flash drive is enough, since the task of hard binding is not worth it, and formatting implies the complete destruction of information, in fact equating the formatted USB flash drive to a new one.
Now let's start implementing the heuristic itself.
Bool IsItABadFlash (AnsiString DriveLetter) (DWORD NotUsed; char drive_fat; DWORD VolumeFlags; char VolumeInfo; DWORD VolumeSerialNumber; GetVolumeInformation (AnsiString (DriveLetter + ": \\\\"). C_str (), NULL, size, & VolumeInerfo) & VolumeFlags, drive_fat, sizeof (drive_fat)); bool badflash \u003d false; if ((String (drive_fat)! \u003d "NTFS") && (FileExists (DriveLetter + ": \\\\ autorun.inf"))) (DWORD dwAttrs; dwAttrs \u003d GetFileAttributes (AnsiString (DriveLetter + ": \\ \\ autorun.inf"). C_str ()); if ((dwAttrs & FILE_ATTRIBUTE_SYSTEM) && (dwAttrs & FILE_ATTRIBUTE_HIDDEN) && (dwAttrs & true_flash); (! badflash) (TSearchRec sr; FindFirst (DriveLetter + ": \\\\ *. lnk", faAnyFile, sr); int filep \u003d sr.Name.LastDelimiter ("."); AnsiString filebez \u003d sr.Name.SubString (1, filep-1); if (DirectoryExists (DriveLetter + ": \\\\" + filebez)) (DWORD dwAttrs \u003d GetFileAttributes (AnsiString (DriveLetter + ": \\\\" + filebez) .c_str ()); if ((dwAttrs & FILE_ATTRIB UTE_SYSTEM) && (dwAttrs & FILE_ATTRIBUTE_HIDDEN)) (badflash \u003d true; ))) return badflash; )
The heuristic function algorithm is quite simple. First, we weed out all devices with file system NTFS and those that do not contain the autorun.inf file. As a rule, all flash drives come with the FAT32 file system by default (less often FAT and even less often exFAT), but sometimes system administrators or other IT staff will format them in nTFS system for your needs. We do not need "smart guys", we immediately exclude them. The next step is to check the autorun.inf file for the "hidden" and "system" attributes. The autorun.inf file may also belong to a completely legitimate program, but if these attributes are present in it, then it is very likely that the flash drive is infected with a virus.
Many virus writers are now less likely to use the autorun.inf file to infect machines. There are several reasons at once: first, almost all antiviruses or users disable the autorun option; secondly, there may be several viruses on the computer that use the same distribution method, and each of them overwrites the file in its own way. Therefore, the method of infection through the creation of shortcuts and hiding the original folders began to be used more and more often. In order not to leave these flash drives unattended, we check for the presence of a shortcut file and the presence of a folder with the same name in the root of the volume. If the folder also has the attributes "hidden" and "system", then we mark this USB flash drive as infected.
Of course, the heuristic has its own errors and nuances, so it makes sense to work it out carefully to specific task, however, in our case, it is possible to assert its correctness with 100% probability.
If with heuristic analysis flash drives are generally clear, then with the "infection" nuances are possible. For example, you can simply overwrite an old virus with ours without any amendments to the autorun.inf file, files, shortcuts, etc. Thus, our "virus" will get control on a new computer, but it is better to make an old copy of the virus and save it in the same directory with a slightly different name. If for some reason an antivirus is running on another computer, it will detect the old virus, remove it, give the user a warning about the successful destruction of the threat - and thus provide a false sense of security for the user, and our "virus" will remain unnoticed.
In addition, in the December issue of Hacker, we also wrote about DLL hijacking vulnerabilities in various software and its effective use. Therefore, if it is assumed that such programs as password managers or portable versions of various software may be on the flash drives, then it makes sense to exploit this vulnerability and thereby expand the range of affected machines and the value of the obtained data for penetration testing.
By the way, it doesn't always make sense to resort to infecting flash drives. For example, if the information security department has the task of simply periodically monitoring employees for the presence of "unreliable people", then it is wiser to establish this program to several machines and just record serial numbers flash drives and the time the malicious file was created to collect statistics. Thus, it is not required to literally search all employees, while maintaining the confidentiality of data on flash drives, and based on the data obtained, one can also judge about possible infection of users' home computers and the state of information security in general. After all, as we wrote earlier, any system is subject to random factors and the risk of threats is not excluded.

Testing
Having deployed the program in a relatively medium-sized network, a week later we received quite eloquent data. More than 20% of all connected flash drives were infected with some kind of virus or trojan, and more than 15% were still infected when reconnected after a couple of days. It should also be noted that many computers had anti-virus protection, which periodically performed its duties. However, the habitual indifference to the pop-up antivirus warning that users have long been accustomed to when connecting a USB flash drive did not allow them to assume that they were dealing with a completely different threat. A false sense of security allowed users to connect a USB flash drive to various computers, and our program successfully does its job.

Briefly about the algorithm
- We install our program on computers in the company.
- We scan plug-in flash drives for signs of infection.
- We "infect" users' flash drives with our test "virus" or rewrite their numbers for statistics.
- We report to the authorities, punish the gouging users, keep them, do not let them in, and prohibit them.
Conclusion
Summing up, we can say that the main drawback of this method is its uncertainty. Nobody knows when exactly the "suitable" flash drive will be connected to the computer, since it strongly depends on the environment in which the program is deployed. However, this disadvantage does not diminish the main advantage of the method. You can go unnoticed for a very long time and, dissolving among other threats, hit more and more new cars completely in automatic mode... It is easy to see that this technique has a certain economies of scale. The more employees work in the organization and the more diverse the internal communications, the greater the result. Although this approach will work perfectly in a structure of absolutely any scale, its main task is reduced not to a massive defeat of the system, but to a targeted strike at the weakest link - a person. ] [
You will be prompted to download the "Virus" at any of the terminals of the Institute. This, in turn, will launch the new Underground and Undercover mission.
Step by step guide to download virus:
1. Find any terminal in the Institute
2. Insert holotape ([R] button)
3. Select "Virus" from the list
4. "Click" all the items in the menu - Network Scan / Message from Volume / Copy encrypted message.
5. Return to the main menu. A new line should appear in it about an urgent response - open - done.
The answer will say the meeting place. We follow the marker on the compass and meet Liam:
After the conversation, he will offer to meet with "his synth", we communicate, we find out that they have 13 more synths who want to escape from the Institute. And Liam has an idea of \u200b\u200bhow to send everyone to the surface at once, but this will require our help - to obtain the requisites for access to the old security system of the Institute of Technology - "Code Defender", which are located somewhere in the Commonwealth.
We go to the subway, talk to Desdemona.

She will ask you to leave a report at the PAM terminal - let's go to it.

We select "Open report about the Institute". Then we talk to the PAM robot, it stands nearby (note: the PAM terminal and the PAM robot are different things).
We are told the place of the next visit - "Cambridge Polymer Laboratory" ", we go there.
In the building we are met by the robot Molly (a rather funny robot that will give additional task "Laboratory" Cambridge Polymer ""). After talking with the robot, we are looking for such a room:

To get there, you will need to either hack the "Difficult" level terminal, or run a little more around the building and find a passage to the room through the upper floor (there will be a hole in the floor).
We get to the desired terminal - there will be many items, we need a "Request for a password (archive)".

To leave the room - open the door using another terminal in the room.
We return to Desdemona, we talk. Then we return to the Institute and talk to Liam and Z1-14.

The latter will say that he needs time to talk to friends. We sit on a bench next to it and scroll through it for 24 hours. Talk to Z1-14 again.
He will say that synths are ready to fight for freedom, but they need weapons that they, in general, can make themselves, but they need materials.
We leave for the tunnel and kill the guards.

Going back to Z1-14, he will say that they are starting to assemble the weapons, but it will take time.
Further, the task will be "on pause" until the Run task is completed. After completing this task, immediately after the meeting of directors, a synth will come up to you and say that in your room later - you urgently need to go there. It's clear that there is no flood, just Z1-14 needs to meet with us.
He will say that the Institute has secretly transferred the location of the underground base to the Brotherhood of Steel, and they urgently need to be warned. We leave for the subway and speak with Desdemona.
This completes the task.
Reward
- 400 (?) Experience
- Nail gun
- Rail Nail (56)
If a text message appears on your computer stating that your files are encrypted, then don't rush to panic. What are the symptoms of file encryption? The usual extension is changed to * .vault, * .xtbl, * [email protected]_XO101, etc. You cannot open the files - you need a key, which can be purchased by sending a letter to the address indicated in the message.
Where did you get your encrypted files?
The computer caught a virus that blocked access to information. Antiviruses often skip them, because this program is usually based on some kind of harmless free utility encryption. You can remove the virus itself quickly enough, but serious problems can arise with decrypting the information.
The technical support of Kaspersky Lab, Dr.Web and other well-known companies engaged in the development of anti-virus software, in response to user requests to decrypt the data, informs what to do acceptable time impossible. There are several programs that can pick up code, but they only know how to work with previously studied viruses. If you are faced with a new modification, then the chances of restoring access to information are extremely small.
How does a ransomware virus get to a computer?
In 90% of cases, users themselves activate the virus on the computeropening unknown letters. After that, a message with a provocative topic comes to the e-mail - "Summons to court", "Loan debt", "Notice from the tax office", etc. There is an attachment inside the fake email, after downloading which the ransomware gets on the computer and gradually begins to block access to files.
Encryption is not instantaneous, so users have time to remove the virus before all information is encrypted. Destroy malicious script can be done using the cleaning utilities Dr.Web CureIt, Kaspersky Internet Security and Malwarebytes Antimalware.
File recovery methods
If the system protection has been enabled on the computer, then even after the action of the ransomware virus, there is a chance to return files to their normal state using shadow copies of files. Cryptographers usually try to remove them, but sometimes they fail due to lack of administrator privileges.
Restore a previous version:

To keep the previous versions, you need to enable system protection.
Important: system protection must be enabled before the ransomware appears, after that it will no longer help.
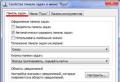
- Open "Computer" properties.

- From the menu on the left, select System Protection.

- Highlight drive C and click Configure.

- Select restore settings and previous versions files. Apply the changes by clicking "Ok".

If you took these measures before the appearance of a virus encrypting files, then after cleaning the computer from malicious code you will have a good chance of recovering information.
Using special utilities
Kaspersky Lab has prepared several utilities to help open encrypted files after removing the virus. The first decryptor worth trying is Kaspersky RectorDecryptor.
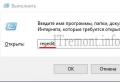
- Download the application from the official Kaspersky Lab website.
- Then run the utility and click "Start check". Specify the path to any encrypted file.
If malware did not change the extension of the files, then for decryption it is necessary to collect them in a separate folder. If the utility is RectorDecryptor, download two more programs from the official Kaspersky website - XoristDecryptor and RakhniDecryptor. 
The latest utility from Kaspersky Lab is called Ransomware Decryptor. It helps decrypt files after the CoinVault virus, which is not yet very common on the Russian Internet, but may soon replace other Trojans.
After the quest will start walkthrough Closed facility Fallout 4... You enter the Institute for the first time. If you work for any faction, along the way you need to complete its task. For the Minutemans and the Brotherhood of Steel - download the virus to the terminal. For the Subway, send a message to the Patriot.
Father
Once inside the building, you will hear a voice that introduces itself as the Father. He will ask you to look around. Take the elevator. After leaving it and walking around a bit, you will find a room with a boy named Sean. After the conversation, it will become clear that this is not your son, but a synth. The head of the institute will also come here - the real Sean. Years did not spare him, because 60 years have passed since the abduction!
Sometimes there is a bug in the quest Closed-type establishment - the conversation with the boy does not start. When faced with a problem, enter console command tcl. This will allow you to walk through the glass wall, talk and exit. Disable passing through obstacles with the same command.
Scientists
Sean will invite you to meet and talk with the scientists of the Institute:
- engineer Ellie Fillmore;
- the head of the department of biosciences, Clayton Holdren;
- the head of the department of control over robots Justin Ayo;
- by Dr. Madison Lee.
Lee is modifying your Pip-Boy so that you can now freely leave the Fallout 4 Gated Institution and return here using Fast Travel. A new marker will become available on the map.
Return to the Father and talk again. He offers to work for the Institute and will give a quest Detention.