The best computer tracking program. Spyware rating PC power-on control
AeroAdmin - is a small application working without installation or configuration. It is launched on local admin and remote client computer and is ready to work, out of the box.
(!) AeroAdmin - remote desktop software that allows you to connect to computers over the Internet or in a LAN from any place and see who is doing what at any moment.
Aside from employee monitoring, the software provides full control to remote computers, including mouse and keyboard control, file transfer etc. You can work with a distant computer as if you were sitting in front of it.
Why AeroAdmin?
FREE for home and business use zero-configuration application
You can be in touch with your employees at any time
Your staff become more responsible at work, as they know they are monitored
You can collaborate interactively
How to configure AeroAdmin for remote employee monitoring?
On employee computer (client):
1. and run AeroAdmin
2.Choose Connection ⇒ Access rights in main menu
3. - Click add in access rights window
4. Type in "ANY" into "ID" and "Name or description" fields. Setup password (you will use it to connect this employee computer). Click Ok.

5. Run AeroAdmin as Windows Service in main menu Connection ⇒ Service.

Configuration of employee computer is finished. You can close AeroAdmin.
On your (operator) computer:
1. and run AeroAdmin
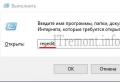
2. Input ID of the computer you want to monitor, as shown on the picture below

3. Choose necessary connection mode, ex "View only"
Many PC users running one of Windows often need programs that monitor your computer.
Such people most often become bosses of various levels, who are subordinate to from a few people to several dozen or even hundreds of employees, working mainly in offices and shops, jealous husbands or wives (girls or boys), parents of children.
AT modern world It is quite difficult to keep track of what a person is doing on the Internet on a smartphone, but it is much easier to set up tracking of user actions on a PC that several people have access to.
Let's look at seven applications that will help collect data on user activity on a computer under control.
We do not compile the top, do not rate the applications and choose the best, but only suggest that you familiarize yourself with the current spies, which are regularly updated and supported.
Note! Spying on someone's actions on a computer is an interference with a person's personal life, so you should not do this unless absolutely necessary, and if you decide to take such a step, be sure to notify everyone you follow about it.
LightLogger
The app is developed by one person and is updated regularly. Great for home use.
Home is meant to monitor the activity of family members or acquaintances who may come to visit, so that something from your computer to do on the internet.
LightLogger features all the classic spy features. It allows you to monitor keystrokes on the keyboard and display data for each program, which will show what messages a person entered in which application, display all his passwords and logins.
Web page monitoring records the history of site visits over time on the page.
Invisible
An important advantage of an elite spy is absolute secrecy. Not only does it not create shortcuts and is not displayed in the taskbar and tray, but it also hides its process from the Task Manager and does not even place a shortcut in the list of frequently launched ones.
Due to the daily update of the program kernel, it is invisible to all antiviruses and anti-keyloggers.
Keystroke recording
Keylogger monitors every keystroke and click of any mouse button.
With these functions, remaining in the shadows, the utility will intercept all typed messages, message texts, electronic documents, will collect everything search queries and data for authorization in the accounts of various Internet pages.
The program code is based on the use of written in Low-level driver assembler, which starts earlier than the Windows graphical shell, which makes it possible to find out the password for the account.

Retrieving browser history
No popular web browser can hide your navigation history. It is easy to track the Internet activity of children and employees with a time stamp (when they visited the site, how long they spent).

Chat recording
As for instant messengers, Elite Keylogger records messages from each of the programs (ICQ clients,) and mail agents in order to provide you with information about who and through what they are communicating with on your computer.
Remote monitoring
After collecting data, reports can be sent to the specified email or an FTP server, making it possible to get acquainted with the actions of subordinates, wife or child, being far from the computer where the keylogger is running. In this way, family members will be more careful, and employees will spend less time in or playing games.
Methods of receiving reports
The received information can be stored on the hard disk of a computer, sent by e-mail or via FTP, forwarded by and even secretly copied to a connected or. The size of the logs is not limited.

Other possibilities
The developers did not refuse to take screenshots, record all running applications with the time of their activity and work in the background. Elite Keylogger's clipboard is also monitored.
Among the considered and similar programs it's hard to choose a clear leader. The functionality of most tracking utilities is similar, only a few developers try to bribe the client with unique features, increased secrecy of the program, design and work with reports.
How do you know what your child or employee is doing on the computer? What sites does he visit, with whom he communicates, what and to whom he writes?
To do this, there are spyware - a special type of software that collects information about all of his actions imperceptibly for the user. Spyware for your computer will solve this problem.

Spyware for a computer should not be confused with a Trojan: the first is absolutely legitimate and is installed with the consent of the administrator, the second gets on the PC illegally and carries out hidden malicious activities.
Although, cybercriminals can also use legitimate tracking programs.
Spy apps are most often installed by business executives and system administrators to monitor employees, parents to spy on children, jealous spouses, etc. In this case, the “victim” may know that she is being monitored, but more often than not, he does not.
Review and Comparison of Five Popular Spyware
NeoSpy
NeoSpy is a versatile keyboard, screen and user activity spy program. NeoSpy works invisibly and can hide its presence during installation.
The user who installs the program has the opportunity to choose one of two installation modes - administrator and hidden. In the first mode, the program is put open - creates a shortcut on the desktop and a folder in the directory Program Files, in the second it is hidden.
Program processes do not appear in Windows Task Manager and third-party task managers.
The functionality of NeoSpy is quite wide and the program can be used both as home tracking and in offices to control employees.
The spyware is distributed in three versions under a shareware license. The price is 820-1990 rubles, but it can work for free (even in hidden mode) with restrictions when viewing reports.
What NeoSpy can do:
- monitor the keyboard;
- monitor website visits;
- show the user's screen in real time via the Internet from another computer or from a tablet;
- take screenshots of the screen and save snapshots from the webcam;
- monitor system events (power on, shutdown, computer downtime, removable media connection);
- intercept the contents of the clipboard;
- Monitor the use of Internet messengers, record Skype calls;
- intercept data sent for printing and copied to external media;
- keep statistics of work at the computer;
- send laptop coordinates (calculated over Wi-Fi).
Thanks to the Russian-language interface, a wide range of functions, correct keyboard interception and a completely hidden operating mode in the system, NeoSpy receives the maximum rating when choosing programs for user control.
Real Spy Monitor
The next spy is Real Spy Monitor. This English-language program has not only tracking functions, but can also block certain actions on the computer. Therefore, it is often used as a parental control tool.
For each account in the settings of Real Spy Monitor, you can create your own prohibition policy, for example, on visiting certain sites.
Unfortunately, due to the lack of an English-language interface, it is more difficult to figure out how Real Spy Monitor works, despite the graphic thumbnails for the buttons.
The program is also paid. The license starts at $ 39.95.
Real Spy Monitor features:
- interception of keystrokes, clipboard contents, system events, websites, messengers, mail;
- work in semi-hidden mode (without an active window, but with displaying the process in the task manager);
- work with multiple accounts;
- selective autostart for different accounts.
In general, many users like Real Spy Monitor, among the shortcomings they note the high cost, the lack of a Russian-language interface and the display of the process in the task manager.
Actual Spy
Actual Spy is positioned by developers as a keylogger (keylogger), although the program can do more than just record keystrokes.
It monitors the contents of the clipboard, takes screenshots, monitors site visits, and so on, which is part of the main set of spies we've reviewed.
When installed, Actual Spy creates a shortcut in the Start menu, so it can be noticed by the user. The launch also takes place openly - to hide the program window, you must press certain keys.
The possibilities of Actual Spy are not much different from those of competitors. Among the shortcomings, users noted that it correctly records keystrokes only in the English layout.
SpyGo
SpyGo is a spy kit for home use. Can also be used in offices to monitor employees.
To start monitoring, just press the "Start" button in SpyGo.
SpyGo is distributed under a shareware license and costs 990-2990 rubles, depending on the set of functions.
AT trial versions monitoring duration is limited to 20 minutes per day, and sending reports to e-mail and FTP is not available.
Key features of SpyGo:
- monitoring keystrokes;
- recording of all actions on the computer (launching programs, operations with files, etc.);
- control of visits to web resources (history, search queries, frequently visited sites, duration of stay on the site);
- recording what is happening on the screen;
- saving the contents of the clipboard;
- listening to the environment (with a microphone);
- monitoring of system events (time of turning on and off the computer, idle time, connecting flash drives, disks, etc.).
Important! The disadvantages of SpyGo, according to users, include the fact that it does not support all windows versions, when sending reports, it often throws errors and is quite easy to unmask.
Snitch
Snitch - the name of this program is translated as "snitch", and is very unfriendly towards the user. Snitch spies on computer activity. It works hidden, does not require complex settings and has little effect on system performance.
The program is released in a single version.
Snitch Features and Features:
- monitoring the keyboard, clipboard, system events, web surfing and communication in instant messengers;
- preparation of summary reports and schedules of controlled events;
- undemanding to network configuration;
- protection against unauthorized termination of the program process;
- monitoring is carried out even if there is no network connection.
Among the shortcomings, you can see conflicts with antivirus software
How to detect a spy on a computer?
Finding spyware on your computer that doesn't show itself outwardly is difficult, but possible.
So, despite the legitimacy, the applications we reviewed can recognize special antiviruses,"Sharpened" for the search for spyware (Trojans with the function of espionage), so we recommend adding installed program to the list of exceptions for such antiviruses.
And if you do not need to remove the spy, but only need to disguise your actions from it, you can use anti-espionage tools that, despite being actively spy on you, will prevent the interception of keyboard events and screenshots.
Then your correspondence and passwords will not fall into the wrong hands.
Hello.
Today's article is devoted more to executives (although if you want to know who is in your absence and how he works at your computer, the article will also be useful).
The issue of controlling the work of other people is rather complicated and, at times, very controversial. I think those who at least once tried to lead at least 3-5 people will understand me now. and coordinate their work (especially if there is really a lot of work) .
But those whose employees work at the computer are a little more fortunate :). Now there are very interesting solutions: special. programs that easily and quickly track everything that a person does during working hours. And the manager will only have to look at the reports. Convenient, I tell you!
In this article I want to tell FROM and TO how to organize such control. So, …
1. Choosing software for organizing control
In my opinion, one of best programs of a kind (to control employees' PC) is CleverControl. Judge for yourself: firstly, to run it on an employee's PC - it takes 1-2 minutes (and no IT knowledge, i.e. no need to ask anyone to help you) ; secondly, 3 pcs can be controlled even in free version (so to speak, evaluate all the possibilities ...) .
C leverControl
Website: http://clevercontrol.ru/
A simple and convenient program for viewing who and what is doing on a PC. It can be installed both on your own computer and on the computer of employees. The report will contain the following data: which websites were visited; start and end time of work; the ability to watch in real time at the PC desktop; viewing applications that the user has launched, etc. (screenshots and examples can be found below in the article) .
In addition to its main direction (control of subordinates), it can also be used for some other purposes: for example, to watch what you are doing yourself, to evaluate the effectiveness of the time spent at the PC, what sites were opened, etc. In general, to increase your efficiency of time spent at the computer.
What else captivates the program is its focus on an unprepared user. Those. if you even just sat down at the computer yesterday, you will not be able to install and configure its work (below, I will show in detail how this is done).
An important point: computers must be connected to the Internet (and preferably high-speed) to be able to control.
By the way, all data and statistics of work are stored on the program server, and you can find out at any time, from any computer: who is doing what. In general, it is convenient!
2. Getting started (registering an account and downloading the program)
Let's get down to business 🙂
First, go to the official website of the program (I gave the link to the site above) and click the " Connect and download for free"(Screenshot below).
Starting to use CleverControl (clickable)
Next, you will need to enter your E-mail and password (remember them, they will be needed to install applications on computers and view the results) , after which you should open personal Area... There you can download the program (the screenshot is shown below).
The downloaded application is best written to a USB flash drive. And then with this flash drive, go one by one to the computers that you are going to control and install the program.
3. Installing the application
Actually, as I wrote above, just install the downloaded program on the computers that you want to control (you can also install it on your PC to make it clearer how everything works and compare your indicators, with the indicators of employees - deduce some kind of benchmark) .
An important point: the installation takes place in standard mode (time required for installation is 2-3 minutes) except for one step. You will need to correctly enter the E-mail and password that you created in the previous step. If you enter an incorrect E-mail, then you will not wait for the report, or in general, the installation will not continue, the program will return an error that the data is incorrect.
Actually, after the installation was completed, the program started working! Everything, she began to track what was happening on this computer, who was behind it and how it was working, etc. You can configure what to control and how through the account that we registered in the 2nd step of this article.
4. Setting the main control parameters: what, how, how much, and how often ...
Remote configuration (clickable)
What can you control?
- what characters were printed;
- what characters have been removed.
Screenshots:
- when changing windows;
- when changing the web page;
- when changing the clipboard;
- the ability to take pictures from a webcam (useful if you want to know if the employee is working at the PC, and if someone is replacing him).
Keyboard events, screenshot, quality (clickable)
In addition, you can control all popular social networks (Facebook, Myspace, Twitter, VK, etc.), shoot video from webcam, control Internet pagers (ICQ, Skype, AIM, etc.), record (speakers, microphone, etc. devices).
And one more nice function for blocking unnecessary actions for employees:
- you can ban social. networks, torrents, video hosting and other entertainment sites;
- you can also manually set the sites to which you want to deny access;
- you can even set stop words to block (however, you need to be more careful with this, because if such a word is found on the right site for work, the employee simply will not be able to access it :)).
Add. blocking parameters (clickable)
5. Reports, what's interesting?
Reports are not generated immediately, but after 10-15 minutes after installing the application on the computer. To see the results of the program: just open the link "Dashboard" (main control panel, if translated into Russian).
Online broadcast (reports) - clickable
You will also have access to dozens of reports on all sorts of criteria (which we asked in the 4th step of this article). For example, the statistics of my last 2 hours of work: it was even interesting to see the efficiency of my work :).
Websites and programs that were launched (reports) - clickable
By the way, there are quite a lot of reports, you just need to click on various sections and links on the panel on the left: keyboard events, screenshots, visited web pages, requests to search engines, Skype, social. networks, sound recording, webcam recording, activity in various applications, etc. (screenshot below).
Report options
An important point!
You can install such software only to control the PCs that you own (or those to which you have legal rights). Failure to comply with such conditions may result in a violation of the law. You should consult with your lawyer about the legality of using CleverControl software in your area of \u200b\u200bresponsibility. CleverControl software is intended only for employee control (employees in most cases, by the way, must give written consent to this).
That's all for this, I will round off. For additions on the topic - thanks in advance. Good luck to all!
In a difficult economic environment, businesses are forced to cut costs and work to improve efficiency. Specialists can come to the rescue here, who help to improve the quality of employees' work.
Improving the efficiency of office workers
The trend towards creating the most comfortable conditions for employees in the office has its side effects - sometimes excessive concern for the team on the part of managers leads to the fact that employees relax and become less efficient. A number of specialized services are used to combat such phenomena.
« Boss Control»
For a long time, turnstiles have been installed at the entrance to most of the office premises, with the help of which it is possible to collect data on the attendance of employees - to enter the office you need to attach a pass. The problem here is that setting up locally running control systems is not the easiest thing to do.
In turn, "Boss Control" is a service that consists of access control terminals and a data processing service. The terminal is hung on the wall, employees use it to check in at the entrance, and then the system generates attendance reports. If an employee is late for no good reason, leaves work early, or often goes on smoke breaks, this will immediately become known. As a result, employees spend more time at the workplace.
Pay punch
Biometric system for keeping track of employees' attendance and time worked. By analogy with the previous tool, a special device is also installed in the office, to which employees put their finger or hand. Thus, the time worked is monitored, which is especially convenient if it is necessary to calculate wages on an hourly basis.
Information about the attendance of employees is automatically transmitted to management and. Since the system is biometric, it will not work to deceive it, for example, by asking a colleague in the office to attach a card of an employee who is absent from it.
CrocoTime
However, the very fact of being in the office and at the workplace does not mean that the employee is working effectively. There is nothing stopping him from “creating the appearance” of hectic activity, actually wasting time on non-work sites or entertainment applications. Losses from such an unproductive pastime can be very significant - according to various estimates, this causes a total damage to the country's economy in the hundreds of billions of rubles a year.
In order to find out what percentage of the employee's working time spent on solving business problems, and how much he “procrastinated” on entertainment resources, the CrocoTime service helps. Based on the collected data, it calculates the productivity rate of each employee, and also provides management with reports on which resources are taking up the most time from employees.
Disciplina.ru
Another system for increasing the efficiency of office employees. Disciplina.ru not only collects information about the programs and applications used, but also monitors compliance with the work schedule, and also records overtime.

Subsequently, reports are created that allow you to understand the structure of the working day of each specific employee - which tasks they spend the most time, in which periods they work more or less. This data helps management to optimize work processes so as not to overburden employees, but also not to allow them to relax excessively.
Control of field workers
Controlling office employees is easier, if only for the simple reason that they are in the same place and, as a rule, the manager can communicate with them quite easily. On-site work is another matter - for example, equipment installation, furniture assembly, cleaning or delivery.
Here, employees often have a lot of freedom, which sometimes leads to problems - for example, poor performance of work or deception ("hack" on the client bypassing the employer using the materials and tools of the company).
To improve the efficiency of mobile workers, as well as to better control them, special tools are used, which are called field management in the West.
Planado.ru
Working on the road means freedom - and this is what mobile workers often value. However, the absence of a boss who stands "above the soul" creates various temptations. From banal deception of the employer - no one will interfere with doing the work, and taking money into your pocket - to mistakes in completing the task due to missing some unimportant, in the opinion of the master, steps.
Field management tools, including the Planado service, are designed to give business leaders the ability to control their employees and set a uniform standard for their work.
To do this, for example, checklists (checklists) help, in mobile application the employee contains information on the order, and also lists all the steps that need to be taken to solve the problem in the best way. This eliminates amateur activities unnecessary when performing the same type of work (which, as a rule, field employees do), and increases its overall quality. In addition, under these conditions, beginners make fewer mistakes and are more quickly drawn into the workflow.

After solving the problem, the employee creates a photo report in the application, which shows that the work is done with high quality (assembled furniture, installed equipment, clean room after cleaning, etc.), and sends it to the office. Thus, the management can immediately see the shortcomings and point out them. In addition, the service is integrated with Yandex. Maps ”, which allows the employer to see the movements of employees in real time and optimize their routes, taking into account traffic jams. This helps to complete more orders per day.
"Mobifors"
The Mobifors service also helps companies monitor their field workers. The tool is designed to work with the 1C: Enterprise 8 system. With its help, managers can quickly distribute tasks between mobile employees, control their movements, track the status of tasks, and also exchange instant messages with them.

In addition, the system collects work performance data and generates employee performance reports that take into account over 30 different metrics.
Task24
The Task24 service provides a kind of exchange for remote orders. With its help, mobile employees can enter the system and sort orders that are more convenient for them to fulfill (however, they can be assigned to a specific employee). After accepting the order, the wizard opens detailed information about the task. In the process of performing work, the employee notes his labor costs in the system.

As in the examples above, the system tracks the location of employees on a map. Based on the results of the work, the system generates reports that can be used, for example, for calculating wages. In addition, an API has been implemented that allows you to upload information to 1C and other systems, as well as integrate Task24 with the software of the call center employees.
Control of remote employees
When working with remote employees (freelancers, personal assistants and so on) the problem of control is one of the main ones. To increase the productivity of such interactions, company representatives can also use specialized software.
JoDo.Im
A simple service with an uncomplicated design. Helps to structure information when working with remote workers and freelancers. The communication between the manager or the customer and the contractor takes place in the Jabber chat, where, using special commands, you can assign tasks to the employee that will not disappear in the communication logs, but will be entered into the database.

So, you can always restore the entire sequence of tasks and subtasks. In this case, the system will not allow the executor to report the completion of the work if any of the subtasks have not been completed.
Tracking plan execution
There are many systems for project management. With their help, managers can track the real performance of an employee, and not only collect information about the time spent in the office or programs used during the day.
Pyrus
The Pyrus service allows you to solve the problem of missing deadlines, which can seriously harm your business - very often even important projects are completed later than the established deadlines, which has various negative consequences for the business.

Pyrus allows you to identify employees who do not meet deadlines. With the help of such software, managers can track tasks and debug business processes, as well as identify employees who do not have time to complete work on time.
Improving the efficiency of restaurant workers
The restaurant business has traditionally suffered from employee abuse and inefficiency. Cases of poor service or trivial theft are common. Restaurateurs seek to overcome these challenges with implementation special tools control.
Jowi
There are a large number of staff control tools for restaurants. Historical such services were divided into cloud services, when all information is stored on a remote server, and local, when all the necessary data is stored directly in the institution. Each type of system had its drawbacks - when using cloud services in case of problems with the Internet connection, the work of the restaurant can stop, and in the case of local placement, careless employees can gain access to the data, which opens the way for abuse.
Therefore, hybrid systems like the Jowi began to appear. They combine both methods of working with data - the system can work locally even without the Internet, and when a connection appears, the data is uploaded to the cloud server.

Such tools help to increase the speed of service by automating the process of receiving an order and transferring it from a waiter to a cook. The usage scenario could be like this: using a tablet with installed application the waiter accepts the order, in the kitchen the cook is immediately shown a list of dishes, and the hall manager can set the time for which he must have time to prepare the order. Then the waiter will also receive a notification on the tablet, and he will go to pick up the order (and will not constantly go to the kitchen to find out how things are with him).
In addition to the automation of work itself, control systems provide the ability to receive reports on all important indicators of the restaurant - data on orders, product balances in the warehouse, etc. All this reduces the likelihood of deception - employees cannot hide part of the proceeds or, for example, steal food from the kitchen and drinks from the bar.