Wireless stress test with Wifi_Jammer: how to jam Wi-Fi. ESP8266 pocket wifi jammer What is wifi jammer
Part 2: Work with Wi-Fi jammer, based on ESP8266
For the module requires power, it can be powered from USB computer port / power supply 5v or as in my case from UMB (PowerBank).
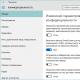
Spoiler: Photo example
Now from any device, we need to connect to an access point pwnetwhich our module created (Password deauther) .
Moving from browser to "any" device at To view the link Login or Register , here we are warned that this thing is legal to use only on your own network:
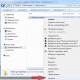
Spoiler: Admin panel


- APs - Search and selection Wi-Fi points access
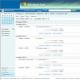
- Stations - After selecting an access point, you can scan it and view all connected devices. I do not know why, but the device did not find raspberries (Raspberry Pi3)... Perhaps this is somehow connected with the fact that the module has a very weak antenna, and simply does not reach it. (Lies 2 meters, in a box)
- Attacks - here we can choose the type of attack. (Description below)
- Settings- Setting up the device, for example, the name of the created network and its password, you can examine in more detail yourself. You can also reboot the device in this tab.
Deauth - Actually herself function-jammer, directed to all access points selected in the first tab.
Beacon - Flood, creating a cloud (Up to 48) wi-fi networks. The networks themselves can be either named / created by you at the bottom of the tab, or created automatically - since there is such a function.
Probe-Request - DDos attack on the access point (I did not find a description of her, I say as far as I understood myself), an extremely useless thing for me. The result of enabling this function: The admin panel of the router is in perfect order, just like it is. You can also connect to the AP, the signal is stable.
My opinion. A fucking huge disadvantage is that this module has a very weak antenna. For its normal operation, buy another module. Unplug this one from the board, insert one, and then you will be able to connect the antenna. I haven’t found another way out yet, perhaps you know - write to me. For as I understand it, if we solder a regular antenna right here, then we will burn this module.
Today, a person's dependence on the Internet is gaining momentum, because now it is impossible to deny the constant connection an individual with a network through which he receives this or that information to meet general education and just entertainment needs. Also, modern man spends a lot of time texting in in social networks or by surfing various web pages. This factor can be used as a so-called lever of pressure on a particular person.
Probably, each of us has ever faced the problem of noisy neighbors with whom it is impossible to build a constructive dialogue about the fact that you can behave a little less loudly. We recommend communicating in a legal way, but if all else fails, then you should act more radically, and most importantly, imperceptibly.
You can, for example, drown out wifi-signal of incomprehensible claims of housemates. This method we will consider in more detail in this article.
The principle of operation of the Wi-Fi jammer and its main manufacturers.
Jammerwifi, or, as it is also called - Wi-Fi suppressor, is designed to implement blocking of working activities various devices, including those carrying out illegal obtaining of certain information. Usually, such devices operate on the basis of standards Wi-Fi and bluetooth.
The main principle of the signal suppressor is the special generation of noise interference in the installed frequency range... A device such as a jammer allows you to implement a smooth adjustment required to suppress the signal router power in any of the ranges. This allows you to implement blocking wirelesssource of which is the router, within the protected premises.
Jammer wifi from the router can prevent wireless transmission data between it and:
- smartphone;
- laptop;
- tablet;
- personal computer;
- other gadget supporting the function wireless network.
The range of such a device, designed to muffle a wifi signal, is directly dependent on the conditions under which it is operated, as well as on the power of the installed signal of the main stations and neighboring terminals. The standard jamming radius for jammers is 30-40 metersand the frequency range of the working activity is 2.4GHz.
The most popular manufacturers of jammers are:
- blockers "LGSh" (701, 716, 718, 702, 712, 704, 719, 705);
- suppressors "Sonnet" (3rd model, 4th model);
- multi-frequency signal suppressors operating in a large number of ranges (Whirlwind, Tsunami). They will help the user jam signals GSM, CDMA, 3G.

We make a jammer with our own hands.
If you do not want to spend money on purchasing a factory suppressorwifi signal, you can easily create the necessary device with your own hands. In order to start assembling the jammer on your own, you need to find a detailed diagram of the device on the Internet.
Further actions are to implement the layout of the main components of the apparatus. The following items should be purchased:
- a generator, the purpose of which is to control voltage;
- antenna that determines the jamming radius;
- special RF amplification unit;
- a tuning circuit with a device installed in it that generates interference.
To suppress wi-fi frequencies, you should purchase a voltage generator that operates in a frequency range of 2.4 GHz up to 2.5 GHz.
You should also pay special attention to the form in which the jammer will be assembled: whether it will be a portable plan or a desktop plan. It should be borne in mind that the table-type blocker has a larger coverage area in contrast to the portable type device.
We jam the Wi-Fi signal with another network.
In order to carry out suppression signal one wi-fi network with another wireless network, you need to install a special kit on your PC or laptop software, with the help of which the detection of all networks available nearby (even hidden ones) is realized. This software includes "Aircrack-ng", which, moreover, is designed to implement the interception of traffic that is transmitted via wireless networks. This program carries out its work with any network adapterworking wirelessly. The main requirement for the adapter is its support for monitoring mode.
The program can work on the basis of such operating systems, as:
- Windows;
- Linux;
- Mac OS X;
- UNIX.
After the software is installed, you should determine the communication channel on which the router, the signal of which must be suppressed. After finding the specified access point, you must turn on your point on the same communication channel. Next, you should increase the signal strength of your network to the maximum parameters.
The consequence of such a simple fraud is a complete drop in the speed of the object to suppress the Internet signal.
Nowadays, silence is the greatest luxury that a modern person can afford. Why? Because mobile phones have become such an affordable attribute of our everyday lifethat it is almost impossible to hide from them. And if you are at a theatrical performance or such a long-awaited concert of classical music, it is simply necessary to muffle your cell phone. From lovers of meaningless phone conversations, who often break such an important silence at this moment, they came up with a new device of innovative technologies called a jammer or jammer for mobile phones.
Cellular jammers or jammers - what are they?
Jammer GSM device or jammer cellular communication Is a universal multifunctional device that acts as a cellular signal blocker. This equipment just perfectly copes with its purpose - to suppress communications in the territory that it serves.
What does a jammer consist of?
The jammer, or jammer, consists of several basic fragments, namely: a microcontroller, an integrating link, a module and an amplifier of the supplied power. Such a device is powered by a battery that is identical to the counterparts used for operation mobile phone... Accordingly, such a battery is attached to the jammer board.
How the jammer works
Now a little about the principle of operation of mobile jammers. Such a device is a signal generator that has no information. Simply put, it's just noise at certain frequencies. This signal or noise is optimally increased by a special power amplifier fitted to the jammers. Accordingly, this noise significantly interrupts the supplied signal and interferes with telephone conversation... So in a simple way you can silence an annoying cell phone.
However, jamming is not the only positive jammer feature. This device is called multifunctional for a reason. This appliance can block wireless Internet, Wi-Fi, 3G and Bluetooth.
Jammer features
The operation of such a cell jammer has several features. This device works only after 15 seconds from the moment of switching on. Accordingly, if you want to interrupt the conversation, then you need to turn on the jammer a little earlier than the connection takes place. You should also consider the coverage area of \u200b\u200bthe phone jammer. This value, on average, is 7-8 meters. Of course, the coverage area can be higher, but it depends on the model you choose.
Scope of communication jammers
This multifunction device densely entered into many spheres of human life. It is actively used in commerce to avoid leakage of confidential information. Business meetings and important business conversations are no longer complete without this innovative device. Customs organizations, law enforcement agencies and correctional institutions actively use the jammer in their work. Educational institutions with the help of a jammer can test the true knowledge of their students, because by drowning out the Internet connection, they make students rely only on themselves, without using external prompts.
A Wi-Fi jammer, or Wi-Fi jammer, is a gadget that is designed to disconnect wireless devices from a hotspot. Why is this needed? You can imagine both a friendly prank (a neighbor, of course, will be delighted when you cut off his porn video or, for example, a football match at the most interesting place), and a criminal application: an attacker can disconnect security cameras or other important equipment from the network. In this article, we will analyze what are the inexpensive options for hardware deauthenticators, how to use them, and how to protect against such attacks.
How the "jammer" works
Unlike real jammers, which interrupt the signal of the radio transmitter with their stronger signal, the deauthenticator works at the software level. It implements a denial of service attack by sending a deauthentication frame to the router on behalf of the devices connected to the network. Since this frame is not encrypted in any way, it is enough for the jammer to find out the MAC addresses of the devices by sniffing the traffic on the network.
Typically, deauthentication is part of a complex network attack. It is used to create an "evil double" access point or to intercept a handshake, which then allows you to decrypt the password. However, a jammer can be useful on its own.
WARNING
All of these tips are highly recommended for educational purposes only. Blocking data transmission and using the considered means may be punishable by law. Penetration testing requires written confirmation from the customer. Remember that deauthorization data is saved in the router logs.
Recently, inexpensive and miniature boards with support for software platform NodeMCU. They are built on the ESP8266 module, which implements work with Wi-Fi using the 802.11b / g / n standard at 2.4 GHz. Now there are two variants of such boards: with the CP2102 chip of the American company Silicon Labs or with the Chinese CH340.

These boards are positioned as devices for prototyping: on their basis, craftsmen create automated systemscontrolled by Wi-Fi. The topic itself is quite exciting, but we are now interested in something else - the possibility of using NodeMCU to conduct attacks.
Due to technical limitations, the ESP8266 is unsuitable for full monitoring and packet injection, but it can be used as a deauthenticator - which led to the appearance of the corresponding firmware. Last year, a good person with the pseudonym Spacehuhn released the first of them, but since then there have been other versions - with additional features... However, before moving on to the software, let's decide on the choice of hardware.
INFO
If you choose more serious wardriving equipment - with a monitoring mode and maybe even the ability to conduct MiTM attacks on the network - then check out our last year.
I will demonstrate the process using the example of a board from the Chinese manufacturer Dstike: it has an ESP8266 and has modes of operation as a client (P2P) and an access point (soft-AP). The board can be controlled from a smartphone or any other device with Wi-Fi.
Note that the performance of the software does not depend on the chip or the board - you can choose any option you like. There are several variants of Dstike products in different designs and for use in different situations. All of them have one thing in common - the ability to jam networks.
Varieties of Dstike devices
Deauther wristband - bracelet with built-in display, battery and switch. Convenient device for quick access to the control panel.

Deauther Power bank - with a modified charge controller; control is carried out through a special panel. The controller has a connector for connection external antenna... Batteries are not included. It is a discreet device that can be easily dropped off and used remotely.


Deauther OLED V3.5 - in this version, you will additionally receive a connector for connecting an external antenna and a holder for a 18650 mAh battery. The device is controlled using buttons and a switch, and the output goes to the screen, which allows you to use this option without additional equipment.

The main advantage of these gadgets is the ability to select a specific network or all at once within the range of the device. Just in case, I would like to point out that you won't need a Wi-Fi password to carry out attacks! 🙂
Installing Deauther 2.0
Let's start with Deauther 2.0 - the very firmware that Spacehuhn developed. In its GitHub repository, you can select the version for a specific board.
Files with the bin extension are compiled sketches. They need to be installed on the board through a special bootloader. But if you want, then in the archives with the source code you will find libraries and sketches that can be delivered through the Arduino IDE.
Continuation is available only to members
Option 1. Join the "site" community to read all the materials on the site
Membership in the community during the specified period will open you access to ALL Hacker's materials, increase your personal cumulative discount and allow you to accumulate a professional Xakep Score!
If you have any proproblems with wireless devices, you should read the article “ ».
Is it possible to jam Wi-Fi?
You (or your organization) took a responsible approach to setting up wireless access points (Wi-Fi): you used, first of all, disabled WPS and came up with a very complex password. Does this mean that now you can relax? No, attackers have at least a couple more tricks up their sleeves - DoS and Wi-Fi jamming. Even if they cannot penetrate your network, they can prevent it from working properly.
This the instruction describes the jamming of Wi-Fi, designed for stress test your wireless network so you can assess the threats and take preventive security measures.
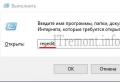
How to start Wifi_Jammer correctly
Name changed after Aircrack-ng update wireless interface... Sorry, Wifi_Jammer has stopped working. But this can be easily corrected by correcting one line. See the details in the article “ ". If you have already edited source Wifi_Jammer, you can continue.
Let's see the name of our interface:
Airmon-ng
Run the following command like this: airmon-ng start interface_name... I have so:
Airmon-ng start wlan0

Please note, I got a warning (you may not have one):
Found 2 processes that could cause trouble. If airodump-ng, aireplay-ng or airtun-ng stops working after a short period of time, you may want to kill (some of) them! PID Name 3036 NetworkManager 3187 dhclient
The program warns that there are conflicts with other applications and that if airodump-ng, aireplay-ng or airtun-ng stops working after a short time, then I need to stop the named processes. You can do it like this (you can have your own numbers - look at the PID):
Kill 3036 kill 3187
We continue:
Airodump-ng wlan0mon

I will train on my own TD - it is at the very top.
Launching WebSploit
websploit Using the wifi_jammer plugin
Wsf\u003e use wifi / wifi_jammer

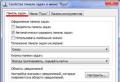
Let's look at its options
Wsf: Wifi_Jammer\u003e show options

We need to set essid, bssid, channel and mon. This data can be taken from the output of airodump-ng.
Wsf: Wifi_Jammer\u003e set essid Mial wsf: Wifi_Jammer\u003e set bssid 20: 25: 64: 16: 58: 8C wsf: Wifi_Jammer\u003e set channel 11
Also required:
Wsf: Wifi_Jammer\u003e set mon wlan0mon
Please note that there are no options here, you need to set the value exactly in wlan0mon.
Run with the command run:
Wsf: Wifi_Jammer\u003e run
There are two ways to control the process. The first is to just make sure your devices are no longer connected to a wireless Wi-Fi network. The second is with the command airodump-ng wlan0mon... Note the field of its output as PWR... Its value during normal operation was in the region of 40.
After the start of the attack, the PWR value is 0 and does not rise until the very end of the attack. Wi-Fi network unavailable at this time.

AT this example we jammed one access point, it is possible to jam all APs at once, for example, with this program.
The essence of the attack is to continuously send deauthentication packets.

Anti-jamming Wi-Fi
- They say there are models of routers that do not pay attention to broadcast deauthentication packets. It might be worth looking for similar models.
- During the attack, you need to understand that the attacker must be in close proximity - no more than a few hundred meters.
- You can configure automatic channel selection at the access point. This should make the attack more difficult, since the attacker will have to take care of channel switching.
- The radical solution is to buy a wired router.
Thank you for attention! Use the received data only for good purposes. This will keep you and other people out of trouble. As always, link sharing is welcome.