Protection of information on computers and computer networks. Ensuring information protection in computer networks. Losses associated with unauthorized access
Information protection– this is a set of measures taken to prevent leakage, theft, loss, unauthorized destruction, distortion, modification (counterfeiting), unauthorized copying, blocking of information, etc. Since the loss of information can occur for purely technical, objective and unintentional reasons, this definition also includes activities related to increasing the reliability of the server due to failures or malfunctions of hard drives, deficiencies in the software used, etc.It should be noted that along with the term "information protection"(in relation to computer networks) the term “computer security” is widely used, usually in a similar meaning.
The transition from working on personal computers to working online makes it more difficult information protection for the following reasons:
- a large number of users on the network and their variable composition. Security at the user name and password level is not sufficient to prevent unauthorized persons from entering the network;
- significant length of the network and the presence of many potential channels of penetration into the network;
- already noted shortcomings in hardware and software, which are often not discovered at the pre-sale stage, called beta testing, and during operation. Including built-in tools that are imperfect information protection even in such well-known and “powerful” network operating systems as Windows NT or NetWare.
The severity of the problem associated with the large length of the network for one of its segments on a coaxial cable is illustrated in Fig. 9.1. There are many physical places and channels for unauthorized access to information on the network. Every device on the network is a potential source electromagnetic radiation due to the fact that the corresponding fields, especially at high frequencies, are not ideally shielded. The grounding system, together with the cable system and power supply network, can serve as a channel for accessing information on the network, including in areas outside the controlled access zone and therefore especially vulnerable. In addition to electromagnetic radiation, non-contact electromagnetic effects on the cable system pose a potential threat. Of course, if you use wired connections such as coaxial cables or twisted pairs, often called copper cables, a direct physical connection to the cable system is also possible. If passwords for logging into the network become known or are guessed, unauthorized login to the network from a file server or from one of the workstations becomes possible. Finally, information can leak through channels outside the network:
- storage media storage,
- elements of building structures and windows of premises that form leakage channels confidential information due to the so-called microphone effect,
- telephone, radio, and other wired and wireless channels (including mobile communication channels).
Rice. 9.1.
Any additional connections to other segments or Internet connections create new problems. Attacks on a local network through an Internet connection in order to gain access to confidential information have recently become widespread due to the shortcomings of the embedded system information protection in TCP/IP protocols. Network attacks over the Internet can be classified as follows:
- A packet sniffer (sniffer - in this case in the sense of filtering) is an application program that uses a network card operating in promiscuous mode (in this mode, all packets received via physical channels are sent to the application for processing by the network adapter) .
- IP spoofing (spoof - deception, hoax) - occurs when a hacker, inside or outside a corporation, impersonates an authorized user.
- Denial of Service (DoS). DoS attack makes the network inaccessible to normal use by exceeding the permissible limits of the network, operating system or application.
- Password attacks are an attempt to guess the password of a legitimate user to log into a network.
- Attacks Man-in-the-Middle type– direct access to packets transmitted over the network.
- Application level attacks.
- Network intelligence is the collection of network information using publicly available data and applications.
- Abuse of trust within the network.
- Unauthorized access (UNA), which cannot be considered a separate type of attack, since most network attacks are carried out to gain unauthorized access.
- Viruses and Trojan horse applications.
Classification of information security tools
Information protection in the network in Fig. 9.1. can be improved through the use of special noise generators that mask side electromagnetic radiation and interference, noise suppression network filters, power supply noise devices, scramblers (encoders) telephone conversations), work suppressors cell phones etc. The radical solution is to switch to fiber-optic connections, which are free from the influence of electromagnetic fields and make it possible to detect the fact of an unauthorized connection.
In general, the means of support information protection In terms of preventing intentional actions, depending on the method of implementation, they can be divided into groups:
- Technical (hardware) means. These are devices of various types (mechanical, electromechanical, electronic, etc.) that solve problems using hardware information protection. They either prevent physical penetration, or, if penetration does occur, access to information, including through its masking. The first part of the problem is solved by locks, window bars, security alarms, etc. The second part is solved by the noise generators mentioned above, surge protectors, scanning radios and many other devices that “block” potential information leakage channels or allowing them to be detected. Advantages technical means associated with their reliability, independence from subjective factors, and high resistance to modification. Weaknesses– insufficient flexibility, relatively large volume and weight, high cost.
- Software tools include programs for user identification, access control, information encryption, removal of residual (working) information such as temporary files, test control of the security system, etc. The advantages of software tools are versatility, flexibility, reliability, ease of installation, ability to modify and develop. Disadvantages - limited network functionality, use of part of the resources of the file server and workstations, high sensitivity to accidental or intentional changes, possible dependence on the types of computers (their hardware).
- Mixed hardware software implement the same functions as hardware and software separately, and have intermediate properties.
- Organizational means consist of organizational and technical (preparing premises with computers, laying a cable system, taking into account the requirements for limiting access to it, etc.) and organizational and legal (national legislation and work rules established by the management of a particular enterprise). The advantages of organizational tools are that they allow you to solve many different problems, are easy to implement, quickly respond to unwanted actions on the network, and have unlimited possibilities for modification and development. Disadvantages: high dependence on subjective factors, including the general organization of work in a particular department.
Introduction
protection information computer network
Information technologies have been actively developing recently and are now developing no less rapidly, increasingly penetrating into all spheres of society. Therefore, the issue of information security becomes more acute. It was not without reason that it was said that “he who owns the information owns the world.” With the emergence of ever new threats and the improvement of methods of unauthorized access to data in information networks, ensuring network security constantly requires close attention.
Such attention consists not only in predicting the actions of attackers, but also in knowledge and competent use of available methods of information security in networks, timely detection and elimination of security gaps.
A feature of network systems, as is known, is that, along with local attacks, there are also opportunities to harm the system by unauthorized access to data thousands of kilometers from the attacked network and computer. Remote attacks now occupy a leading place among serious network security threats. In addition, not only an individual computer can be attacked, but also the information itself transmitted over network connections.
Using various methods and means of information network protection, it is impossible to achieve absolutely ideal network security. There can never be too many security measures, however, as the level of security of a particular network increases, certain inconveniences in its use, restrictions and difficulties for users arise, as a rule. Therefore, it is often necessary to choose the optimal network protection option that would not create great difficulties in using the network and at the same time provide a decent level of information protection. Sometimes creating such an optimal security solution is very difficult.
The relevance of the topic of this final qualifying work is determined by the fact that the issues of information security in networks have always been and are very important; the security of information on the network is one of the main components of its proper functioning. Methods and means of such information protection must be constantly improved, taking into account new emerging threats to network security and gaps in its protection. Therefore, in the opinion of the author of this work, the issues of methods and means of protecting information in networks have remained and remain relevant as long as there are threats to the security of information in networks.
In addition, it should be noted that since today there are a certain number of very different methods and means of protecting information in networks, it is often very important for the system administrator to choose the most effective and efficient methods and means that would ensure security taking into account existing threats and forecasting dangers that may threaten the network. To do this, you need to study existing methods and means of protecting information in networks.
The object of study of this work is the security of information in computer networks, which is ensured by their protection.
The subject of research in this final qualifying work is all those methods and means used in practice that make it possible to ensure the protection of information in networks.
The purpose of this work is to consider existing and applied methods and means of protecting information in networks, namely the main issues and concepts of protecting information in networks, types of threats to information security in networks, not only software, but also legal methods and means of protection. It is also necessary to consider specific issues of software protection of information in corporate networks that exist software solutions in this area.
Based on the goals set in the work that need to be achieved, we will establish the main tasks of this final qualifying work that will need to be completed:
consider the basic concepts of information security in networks and the types of existing threats;
identify some security features of computer networks;
analyze the main methods and means of protecting information in networks;
study existing specific means and methods of software protection of information in networks, the features of protection in various networks;
analyze the effective protection of a specific computer network using the example of a real enterprise LLC NPO Mekhinstrument.
To achieve all goals and objectives set in the work, analysis methods will be used scientific literature, a method of synthesis, comparison, collection and sampling.
When writing the final qualifying work, a wide range of scientific literature was used as a theoretical basis.
Main part
1. Theoretical aspects of information security in networks
.1 Main network security threats
With the development of new computer technologies and communications, information security becomes mandatory. In addition, information security is already one of the main characteristics of information systems (IS). It is no longer a secret that there is a very large class of information processing systems, in the use and development of which the security factor plays a very important role. Such information systems include government, banking, some commercial, military and others.
So, considering the topic of our work, let’s define what IS security is.
The concept of IS security is usually understood as the state of the system’s security from accidental or intentional interference. normal process its functioning, from attempts to obtain unauthorized information, modification or physical destruction of its components. Simply put, it is the ability to counteract various disturbing influences on the IP.
Threats to information security are actions or events that can lead to unauthorized access to information, its distortion, or even destruction of the information resources of the managed system, as well as software (soft) and hardware (hard).
There is also the concept of vulnerability of a computer system, which should be understood as its unfortunate characteristic that makes possible occurrence threats.
To cause harm (unauthorized access, changing information, disabling software and hardware, etc.), an attack is used on a computer system. An attack in this case is an action taken by an attacker, which consists of searching for and exploiting a particular vulnerability in the system.
Typically, there are three main types of security threats: disclosure, integrity, and denial of service threats. Let's take a closer look at each of them.
The threat of disclosure means that information may become known to someone (or those) who should not know it. Very often, instead of the term “disclosure”, “leakage” or “theft of information” is used.
A threat to information integrity is any intentional modification of data stored in a computer system or those transmitted through communication channels from one system to another. As a rule, it is believed that government structures are most often exposed to the threat of disclosure, and business (commercial systems) are more susceptible to the threat to integrity.
There is also a threat of denial of service to the system. Such a threat occurs every time when, as a result of certain actions, access to certain computer system resources can be blocked. Such blocking can be permanent so that the resource cannot be obtained at all, or it can be long enough so that during its unavailability this resource is no longer in demand. In such cases, it is customary to say that the resource has been exhausted.
It should be noted that in local computing systems ah (BC) the most frequent threats are integrity and disclosure threats, and in global ones the dominant place is occupied by the threat of denial of service.
Based on the classical consideration of the cybernetic model of any controlled system, we can say that disturbing influences on it can be random. Among the threats to information security, there are accidental threats, which are also called unintentional and intentional threats. The source of unintentional threats can be hardware failure, actions of employees (without malicious intent), administrators or users of information systems, unintentional errors in software, etc. Such threats also need to be taken into account, since the damage from them is often no less significant.
Intentional threats, on the contrary, are based on malicious intent, often with a specific benefit for the attacker who harms the system through his actions.
An attacker who is trying to intrude or disrupt operations information system, to gain unauthorized access to data is usually called a cracker, and sometimes a “hacker” (from the English “Hack” to break, crack).
When carrying out their illegal actions, hackers strive to find such sources of confidential information that would provide them with the most reliable information in the maximum volumes and at minimum costs to receive it.
Protection against such deliberate threats is a kind of competition between the knowledge and skills of the attacker of the system and its defender. The winner is the one who has more knowledge, skill, experience and the ability to predict the opponent’s actions.
Today we can safely state that it is being born new technology- technology of information protection in computer information systems and data transmission networks. The implementation of this system is very complex and requires quite a lot of effort, but it is very necessary. Proper implementation of this technology allows you to avoid significantly greater damage that may arise from the actual implementation of IP and IT threats.
Deliberate threats to information security are divided into passive and active. Passive threats are illegal actions that an attacker can commit, aimed at gaining unauthorized access to IP resources. However, its functioning is not affected. As an example, unauthorized access to files, databases, launching spyware, etc.
There are also active threats. They are aimed at disrupting the very functioning of the IS through targeted impact on one or more of its components. Active threats include, for example, disabling a computer or its software, changing information in the database, violating correct operation Software, disruption of communication channels, etc. As a rule, the source of an active threat is the actions of burglars, hackers, virus programs, etc.
Intentional threats are also usually divided into internal (arising within the managed organization) and external, which arise from outside the system.
Internal threats that exist within a system or organization are very often determined by social tension and a difficult moral climate.
External threats can be determined not only by the deliberate illegal actions of competitors, the economic environment, but also by other reasons, such as natural disasters.
Let's consider the main threats to information security and the normal functioning of information systems:
compromise of information;
refusal to provide access to information;
illegal use of privileges.
When carrying out some illegal actions, confidential information may be leaked. This concept implies the uncontrolled release of confidential (secret) information beyond the boundaries of the information system or the circle of persons to whom it was entrusted through service or became known in the course of work. Leakage of such information may result from:
Intentional disclosure of confidential information;
Care of information through various technical channels;
Unauthorized access to confidential information in various ways.
It should be noted here that the disclosure of information by its owner or holder is both intentional and careless actions of officials, users, to whom the relevant information was duly entrusted through service or work and which led to the familiarization with it of persons who should not know this information. In addition, uncontrolled loss of confidential information through visual-optical, acoustic, electromagnetic and other channels is possible.
Frequently mentioning the concept of unauthorized access in this work, we will try to define it. Unauthorized access to information is the unlawful deliberate acquisition of confidential information by a person who does not have the right to access protected information.
There are various ways of unauthorized access, let's consider the main ones:
interception of electronic radiation;
the use of "bookmarks" of listening devices;
remote photo and video surveillance;
printer text recovery;
reading residual information in system memory after executing authorized requests;
copying storage media by overcoming security measures;
disguise as a registered user;
masquerading as system requests;
use of software traps;
illegal connection to equipment and communication lines of specially designed hardware that provides access to information;
malicious disabling of protection mechanisms;
decryption of encrypted information by special programs;
information infections.
To carry out unauthorized access along the paths listed above, quite a lot of special technical knowledge is required. As for the causes of leakage channels, they are often structural and technological imperfections in circuit solutions or operational wear of elements. All this allows hackers to create converters operating on certain physical principles, forming an information transmission channel inherent in these principles - a leakage channel.
In addition to unauthorized access through paths that require special knowledge, software and hardware development, there are also quite primitive ways of unauthorized access, we list them:
theft of storage media and documentary waste;
proactive cooperation;
probing;
inducement to cooperation on the part of the burglar;
eavesdropping;
observation.
You should always remember that absolutely any, even minor, information leaks can cause great harm to the organization. Although information leakage can be created using special means interested parties, yet most information leaks occur due to basic shortcomings in the security system and negligence of employees. Some reasons and conditions that may create preconditions for the leakage of trade secrets include:
poor knowledge by the organization’s employees of the rules for protecting confidential information and lack of understanding of the need for their careful compliance;
use of uncertified technical means for processing confidential information;
weak control over compliance with information protection rules by legal, organizational and engineering measures;
staff turnover;
organizational shortcomings, as a result of which the culprits of information leakage are people - IS and IT employees.
1.2 Malicious software and its effects
Of course, the main threats to network security are related, one way or another, to software.
Most of the above paths of unauthorized access can be prevented and blocked with a well-implemented protection and security system; a more significant difficulty is the fight against information infections - malware.
A large number of malicious programs are constantly being created, developed and updated, the main task of which is to steal, change or delete information in the database (DB), computer software, or even harm their hardware. The main difficulty here is that there is no permanent and sufficiently reliable protection against such programs. In the next chapter of the work, existing means of protection will only be examined in more detail.
Now let's briefly look at the classification of malware. All malicious programs can be classified as follows:
Logic bombs. They are used for fraud or theft, using a logic bomb to distort or destroy information. As practice shows, logic bombs are most often used by employees who are dissatisfied with something in the organization and who are soon planning to quit. However, these may also be consultants who serve with certain beliefs, often even suffering from certain mental illnesses.
Giving an example of a logic bomb, we can say that it could be a programmer who is soon facing dismissal; he makes certain changes to the payroll program that begin to act, harming the system, as soon as his name disappears from the database about the company’s employees.
One of the most dangerous types of malware is the Trojan horse. A Trojan horse is a program that, in addition to its main documented function, does something else that is bad. In this case, it is not for nothing that its name is associated with the ancient Greek Trojan horse; the principle of its operation is similar. Under the guise of an ordinary program, a great threat lurks.
Trojan horse - yes additional block commands, inserted in a certain way into the original ordinary (often even useful) program, which is then transmitted to IS users. This block of commands can be triggered when a certain condition occurs (date, time, by external command, etc.). Anyone who runs such a program puts both their files and the entire IP at risk. A Trojan horse usually acts within the authority of one user, but in the interests of another user or even a stranger, whose identity is sometimes impossible to establish.
A Trojan horse can be very dangerous when it is launched by a user who has an extended set of rights and privileges in the system. In this case, the Trojan horse is given much more possibilities to carry out their actions. The attacker who created this Trojan horse is granted all the rights and privileges in the system that the user who launched the program has.
Often when talking about malware, the term “computer virus” is used. A virus is a program that can “multiply” and infect other programs by including in them a modified copy that has the ability to reproduce further.
Usually characteristic features viruses are the following:
) the ability to reproduce - the hidden introduction of its copies;
) the ability to interfere with the computing process.
In addition to Trojans and logic bombs, there are so-called worms. A worm is a program that can spread through a network; it usually does not leave a copy of itself on media. The worm uses the network's support mechanisms to determine which host it could infect. Then, using the same mechanisms, it transfers its “body” or part of it to this node and either activates or waits for suitable conditions for this. The most famous “classical” representative of this class is the Morris worm, which infected Internet network in 1988. A suitable environment for a worm to spread is a network where all users are considered friendly and trust each other, and there are no protective mechanisms. The best way Worm protection is taking precautions against unauthorized access to the network.
Password interceptors (keyloggers) are programs specifically designed to capture passwords. The principle of operation of such programs is that when the user tries to access the system terminal, the information necessary to end the work session is displayed on the screen. When attempting to log in, the user enters a name and password, which are sent to the owner of the invader, after which an error message is displayed and input and control are returned to the operating system. This can be implemented, for example, when gaining access to a database. A user who thinks he made a mistake when typing his password logs in again and gains access to the system. At this time, the name and password are already known to the owner of the password interceptor program.
However, password interception is also possible in other ways. There are also so-called keyloggers, which are spyware, which monitor the sequence of keystrokes in certain programs. Such interceptors transmit such data to the program owner, who, based on such data, can find out the password, login or other information that was entered from the keyboard. To prevent such threats, you must always check before logging into the system that you are entering your name and password specifically to the system input program, and not to a third party that is unknown.
One of the most common and dangerous network attacks is a DDoS attack. Distributed denial of service attack. As a result of the attack, service to legitimate users, networks, systems and other resources is disrupted or completely blocked.
Most DDoS attacks exploit vulnerabilities in the core Internet protocol (TCP/IP), namely the way systems handle SYN requests. There are two basic type attacks that cause denial of service. As a result of the first type of attack, the operation of the entire system or network stops. The hacker sends data or packets to the system that it does not expect, causing the system to stop or reboot. The second type of DDoS attack leads to system overload or local network using a huge amount of information that cannot be processed. The attack consists of continuously accessing the site from many computers located in different parts of the world. In most cases, these computers are infected with viruses, which are controlled centrally by scammers and united in one botnet. Computers that are part of the botnet send spam, thus participating in DDoS attacks.
One type of information infection is information compromise. It is usually implemented through unauthorized changes to the database, as a result of which its user is forced to either abandon it or make additional efforts to identify changes and restore true information. Using compromised information, the consumer is exposed to the risk of making wrong decisions, which is often the goal of attackers.
Unauthorized use of information resources can pose a serious security threat. It may be caused by the consequences of its leak or be a means of compromising it. On the other hand, it has independent significance, since it can cause great damage to the managed system (up to complete IT failure) or its subscribers. Erroneous use of information resources, although authorized, may nevertheless lead to the destruction, leakage or compromise of said resources. This threat is most often a consequence of errors in IT software.
Absolutely any secure system contains tools for use in emergency situations. There are also means with which the system could function in case of violation of the security policy. For example, in case of an unexpected audit, the user must be able to access all sets of the system. Typically, such tools are used by administrators, operators, system programmers, and other users who perform specialized functions.
Most security systems in such cases use sets of privileges, i.e., to perform specific function a certain privilege is required. Typically, users have a minimum set of privileges, while administrators have the maximum.
Privilege sets are protected by a security system. Unauthorized (illegal) seizure of privileges is possible if there are errors in the security system, but most often occurs in the process of managing the security system, in particular when privileges are used carelessly.
Strict adherence to the rules for managing the security system and adherence to the principle of minimum privileges allows you to avoid such violations.
1.3 Network security measures and protections
When considering methods and means of protecting information, we often have to talk about an information security system. An information security system is a whole complex of means, methods and measures to protect information. The creation of such an information security system (ISS) in IS and IT is based on certain principles, which we will consider below.
The first principle of the organization is a systematic approach to building a protection system. A systems approach is an optimal combination of interconnected software, physical, organizational, hardware and other properties, which are confirmed by the practice of creating domestic and foreign security systems and used at all stages of the information processing technological cycle.
One of the main ones is the principle of continuous development of the security system. The principle of continuous development of the security system is very relevant for ISS. As you know, methods of causing harm to IP are constantly being improved; attackers are coming up with new ways to gain unauthorized access to the system and cause damage to it. At the same time, methods of protection must be developed accordingly. Defects in the security system and security gaps must be constantly eliminated, and software and hardware protection systems must be modernized. Therefore, only continuous development of the system will help protect the system effectively.
The principle of separation and minimization of powers for access to processed information and procedures for its processing implies the provision of users and IS employees with the powers necessary only for them to perform specific tasks. That is, there should not be excessive powers in this case.
The principle of complete control and registration of unauthorized access attempts implies constant control over users who try to commit unauthorized actions in the system. Constant security monitoring.
The principle of ensuring the reliability of the security system assumes that it is impossible to reduce the level of reliability of the functioning of the IS in the event of hacking attempts, system failures, or failure of equipment and software. This often requires the creation of a system of continuous security monitoring.
The principle of providing all possible means of combating malware (viruses). This principle implies a set of measures to protect the system from the effects of such software. In particular, protecting the system with anti-virus programs, eliminating possible ways of penetration of viruses, constantly updating and optimizing the operation of anti-virus software. virus programs.
When ensuring the security of any information system, the principle of economic feasibility of using a security system must be observed. This principle is expressed in the fact that possible damage from the impact of threats should exceed the costs of creating and maintaining an information security system.
So, now we will try to determine what are the characteristics of an information system that does not have problems in ensuring information security; thus, such an information system should have the following characteristics:
have information of varying degrees of confidentiality;
have a cryptographic system for protecting information and confidential data;
have a hierarchy of powers of subjects of access to programs and components of IS and IT;
mandatory management of data flows in local networks and during their transmission via communication channels over long distances;
the presence of a system for recording and recording unauthorized access attempts, logging events in the information system and documents published in print;
availability of a system for ensuring information integrity in IT;
availability in the IS of the necessary means of information recovery. In particular, recovery of information from magnetic media;
Availability of storage media accounting tools;
the presence of physical protection of fixed assets and IP objects;
the presence of a separate, special information security service.
When considering the structure of the ISS, a traditional approach is possible, which would highlight the subsystems that provide it.
Target functions in an information security system must have certain types of their own software and other software, relying on which the system will carry out its protective functions. Next, we will consider in more detail the types of such security.
To ensure security, legal support must be present. It represents a set of legal and by-laws, job descriptions, regulations, guidelines, the requirements of which are mandatory in the field of their information protection activities.
Organizational support is of great importance. In this case, such support means the implementation of information security with the help of certain structural units (security, security service, etc.)
Information support includes information, parameters, indicators and data that form the basis for solving problems that ensure the functioning of the ISS.
Hardware is a system of equipping with the necessary technical means sufficient for the functioning of a sufficiently effective security system.
NIB is also based on mathematical support, which is mathematical methods used in various calculations to assess the danger of technical means owned by attackers, to calculate the standards of sufficient protection.
Linguistic support implies the presence of a system of special language means of communication between specialists and users in the field of information security in an organization.
And finally, the normative and methodological support includes norms and regulations for the activities of services, bodies and means that implement information security functions, which represent various types of methods for ensuring information security.
It should be noted that of all protective measures, organizational measures currently play the leading role. Therefore, the question arises about organizing a security service.
Let us now consider specific methods and means of ensuring information security.
One of the main methods of defense is the obstacle method. It is based on physically blocking an attacker’s path to protected information (hardware, etc.).
Access control method is a method of protecting information by regulating the use of all IT and IS resources. Such methods help protect against unauthorized access to information. Access control itself is not simple and has following functions protection:
assigning a personal identifier to each object (user identification);
establishing the authenticity of an object or subject using the identifier presented to them;
verification of authority, that is, verification of compliance of the day of the week, time of day, requested resources and procedures with the regulations;
creation of certain working conditions in the established regulations;
logging all access to protected resources;
timely response when attempts at unauthorized actions are detected.
When transmitting data over communication channels, it is very important to use encryption mechanisms to protect information. The encryption mechanism is a cryptographic locking of information. The encryption method is used both during transmission and during processing and storage of data on storage media. It should be noted that this method is particularly reliable.
The most important protection function is the function of countering attacks by virus programs, which involves a whole range of various measures and the use of anti-virus programs and, if necessary, restoration of the IP after a virus attack.
The set of technical means of protection is divided into physical and hardware.
Physical means of protection include all kinds of engineering devices and structures that prevent attackers from physically penetrating security facilities that protect personnel, material assets and finances, and protect confidential information. Examples of physical protection include burglar alarms, video surveillance, door locks, etc.
The hardware is technical devices to protect information systems that are built directly into information technology or interfaced with it via standard interfaces.
Software tools are a set of special programs and software packages designed to protect information in IS. Such software is usually associated with the software of the IS itself.
Speaking about security system software, it is also necessary to highlight software that implements cryptography (encryption) mechanisms. Cryptography is the science of ensuring the secrecy and/or authenticity of transmitted messages. Authenticity is also called authenticity.
There are also organizational, legislative and morally ethical means of protection.
Organizational means regulate production activities in the IS in such a way that information leakage becomes impossible and all processes in the IS are controlled by its management.
Legislative remedies are determined by the legislation of the country, which regulate the rules for the use, processing and transmission of information limited access and sanctions are established for violation of these rules.
There are also moral and ethical means of protection, just as all sorts of rules and norms of behavior that traditionally developed earlier are taking shape as IP and IT spread throughout the country and the world. Such tools may be developed intentionally.
Moral and ethical standards can be unwritten (the moral qualities of a person) or formalized in a special set (charter) of rules or regulations. These norms are usually not legally approved, but their non-compliance leads to a decline in the prestige of the organization, so they are considered mandatory. A typical example of such regulations is the Code of Professional Conduct for Members of the US Computer Users Association.
A rather important issue in information protection is the issue of legal support in the field information technology. Legal protection of information is one of the areas of ensuring the security of an organization as a regulatory category that determines the measure of protection of its interests from unauthorized access to information.
When resolving controversial issues in the field of information protection, a large role is given to legal norms; disagreements in this area can arise at various levels. In addition, the organization must establish a legally formalized system of disciplinary measures that would make it possible to apply penalties or sanctions to violators of the enterprise’s internal security policy and establish fairly clear conditions for ensuring the confidentiality of information.
Criminal liability for the creation and distribution of computer viruses has now been accepted in most Western countries. Responsibility for such an act may be borne not only by the direct developer, but also by the perpetrators and accomplices.
Let's consider illegal acts that fall under the elements of offenses provided for in certain articles of the Criminal Code Russian Federation(hereinafter referred to as the Criminal Code of the Russian Federation) and the Code of Administrative Offenses of the Russian Federation (Administrative Code, Code of Administrative Offenses).
Such acts include the following:
unauthorized modification of data (deletion, insertion, replacement or rearrangement of data carried out without the knowledge of the owner);
computer sabotage (interfering with activities important for an enterprise or person);
damage to property (if the damaged property is the computer itself or its component);
espionage (providing access for oneself or another person to data not intended for use by these persons and access to which is protected in a special way);
falsification of documents (if the virus changes data intended to prove a particular status or right of a given person or group of persons).
The Criminal Code of the Russian Federation defines several articles on crimes in the field computer information(Articles 272 - 274), which are classified as crimes encroaching on public safety and public order. This type of crime is directed against that part of the established order of social relations that regulate the production, use, distribution and protection of computer information.
Thus, Article 272 of the Criminal Code of the Russian Federation provides for liability for unlawful access to computer information if this entails the destruction, blocking, codification or copying of information. It is important that there is a causal connection between unauthorized access and the onset of consequences, therefore a simple temporary coincidence of the moment of failure in a computer system, which may be caused by malfunctions or software errors, does not entail criminal liability.
Article 273 of the Criminal Code of the Russian Federation provides for liability for the creation, use and distribution of malicious computer programs. The most common types of malware are computer viruses and logic bombs. A virus is just one such program. To be held accountable, it is not necessary that any negative consequences occur; criminal liability occurs as a result of the creation of the program, regardless of whether this program was used or not. The presence of source codes for malicious programs is already grounds for prosecution. The maximum punishment for the offender in this case will be imprisonment for up to three years.
Article 274 of the Criminal Code of the Russian Federation defines liability for violation of the rules of operation of computers, systems and networks, consisting of failure to comply with the rules of operation. This criminal provision does not contain specific technical requirements. This article cannot be used over the Internet; its effect applies only to local networks of organizations.
It should be noted that work in the field of modern information technologies in Russia is carried out by the State Technical Commission (Gostekhkomission) under the President of the Russian Federation. As part of a series of guidance documents (RD) of the State Technical Commission, a draft RD has been prepared, establishing the classification of firewalls (firewalls, or firewalls) according to the level of security against unauthorized access (NSD).
2. Ensuring information security in the telecommunications network of NPO Mekhinstrument LLC
.1 Description of the enterprise network and its features
For the practical part of this work, the limited liability company scientific and production association “Mekhinstrument” (hereinafter referred to as NPO Mekhinstrument LLC) was chosen, using the example of which it will be proposed to organize its effective protection from most existing and current security threats.
NPO Mekhinstrument LLC is located at Pavlovo st. Chapaeva 43, Pavlovo, Nizhny Novgorod region, 606100, Russia
The company has been producing gardening equipment for several years. In particular, the company produces winter shovels, engines, scrapers, etc. for removing snow from streets and roofs of houses. NPO Mekhinstrument also produces installation tools for various purposes - axes, screwdrivers, pullers, pliers, forks and other consumer goods. This is not a complete list of quite popular products in their category on the market. Therefore, the company is developing quite successfully to this day.
The company contains information that constitutes a trade secret, such as:
Materials about discoveries and inventions made at the enterprise and of great scientific importance.
Information about potential customers.
Specific information about contractors and performers of research and development work, the work they perform, their full names and affiliations.
Data on the balance of income and expenses for the enterprise
Data revealing price levels and limits for goods whose sales for the current year have not yet been completed.
NGOs have their own local network, to which only employees have access. In most cases, you only have access to limited number sites of this network necessary in the course of work. Information about each access to the network is recorded by the system administrator. This also applies to the Internet.
The number of workstations in the network is 24. They are combined into several work groups:
director of the enterprise - one workstation;
secretary - one workstation.
sales department - 4 workstations;
supply department - two workstations;
technologists department - 4 workstations;
design department - 3 workstations;
HR department - two workstations;
enterprise accounting - 7 workstations;
Appendix A of this work presents a network diagram of the administrative part of this enterprise; it has a “star” topology.
According to the “star” topology, which was initially chosen by the developers for this network, each workstation is connected to the central network hub (hub) with a separate network cable segment ( twisted pair).
Such a network exhibits a fairly high resistance to failures that can occur if one of the network cables(the network remains operational, only the workstation to which the damaged cable is connected does not work). It is also important that failures on any specific computer ( workstation) networks do not cause problems for the entire network. It is quite easy to put a new workstation into operation with this topology; the network as a whole is well managed.
The only disadvantages that should be noted are the high cable consumption when building a network and the fact that a failure of the hub can lead to a malfunction of the entire network.
Therefore, it is believed that the choice of network topology for a given enterprise is most optimal.
This enterprise network uses the CSMA/CD access method. Exactly this method access uses the Ethernet network architecture that is used in the enterprise.
As already mentioned, the network is built on the basis of twisted pair cable - 10Base - T using Siemon cable, UTP (Unshielded Twisted Pair) Category 5 standard, the international standard for Cabling Systems.
The software basis of the network consists of two operating systems - Windows Server 2003 installed on the server and Windows XP SP3, which is installed on all 24 workstations.
.2 Physical and organizational and legal methods of information protection
Therefore, in any enterprise it is very important to provide protection, first of all, from physical access of unauthorized persons to the local network, which can sometimes cause even more harm than the most dangerous malware - for example, stealing a server, workstations, damaging cables, etc. In addition, fire or explosion may cause damage.
To begin with, let's highlight the main objects in the enterprise that need protection from an information security point of view:
local network server;
automated employee workstations;
directly confidential information (printed, electronic documents, databases, etc.);
access to the office of the director, chief engineer, chief technologist;
other premises with confidential information (for example, accounting).
Therefore, the enterprise has taken the following physical security measures:
security and access control to the territory of the enterprise are carried out, an agreement has been concluded with a security company;
Covert video surveillance is carried out in areas most vulnerable to penetration by unauthorized persons;
a fire safety regime, an evacuation plan, and an autonomous fire warning system have been developed.
Also, organizational and legal methods of ensuring information security are very important. In particular, at this enterprise:
Developed job descriptions all employees, which clearly regulate their rights and responsibilities in various situations;
The lawyer and the personnel inspector have developed additional agreements to all employment contracts of employees, which oblige them to comply with the confidentiality regime of internal information of the enterprise;
There are instructions for protecting the territory of the enterprise, working with alarms and video surveillance, which must be strictly followed by security;
There is a detailed description technological process processing computer information at the enterprise;
There is a provision on confidential document flow, which employees are familiarized with in accordance with the procedure established by law.
In addition, the legal support for the system for protecting confidential information includes a set of internal regulatory and organizational documentation, which includes such enterprise documents as:
Charter of the Limited Liability Company;
collective labor agreement;
employment contracts with employees of the enterprise;
internal regulations for company employees;
job responsibilities of managers, specialists and employees of the enterprise.
instructions for users of information computer networks and databases;
instructions from employees responsible for information security;
employee memo on maintaining commercial or other secrets;
other contractual obligations.
Almost all of the regulatory documents listed above, in one way or another, contain rules that establish mandatory rules for everyone to ensure the required level of information security in the enterprise.
In addition, legal support makes it possible to resolve many controversial issues that inevitably arise in the process of information exchange at various levels - from speech communication to data transmission in computer networks.
A legally formalized system of administrative measures is being created that makes it possible to apply penalties or sanctions to violators of internal security policy, as well as to establish fairly clear conditions for ensuring the confidentiality of information used or generated in cooperation between economic entities, their fulfillment of contractual obligations, joint activities, etc. .
At the same time, parties that do not comply with these conditions bear responsibility within the framework provided for both by the relevant clauses of inter-third-party documents (agreements, agreements, contracts, etc.) and by Russian legislation.
2.3 Software methods for providing protection against threats
We should dwell in more detail on software methods for protecting information in networks. First of all, network protection from security threats in this sense must be ensured at the operating system level.
This company has organized such protection. In particular, this applies to standard tools that are built into operating system. As previously stated, the Windows 2003 Server operating system is installed on the server of our enterprise.
Let's look at the standard security features of this OS that help us ensure protection:
Security Event Log .2003 Server allows you to define what will be audited and written to the security event log whenever certain actions are performed or files are accessed. The revision item shows the action performed, the user who performed it, and the date and time of the action. This function allows you to control both successful and unsuccessful attempts at any action (attempts of unauthorized entry, etc.).
Security event logging for enterprise settings is mandatory so that if there is an attempted network hack, the source can be traced. But logging itself is carried out only in relation to suspicious users and events.
It is quite clear that if absolutely all events are recorded, the volume of registration information will grow catastrophically quickly, and its effective analysis will become impossible.
Tracking is important primarily as a preventive measure, similar to how a security guard at a checkpoint keeps a log. It is hoped that many will refrain from committing security breaches knowing that their actions are being recorded.
Encrypting File System (EFS).
This encrypted file system makes it possible to significantly strengthen information security by directly encrypting files and folders on NTFS volumes. The system works only with those disk volumes that have access rights.
Encryption principle file system EFS is such that folders and files are encrypted using paired keys. Therefore, any user who wants to access files and folders must have a special private key to decrypt the data. Accordingly, without this key it will be impossible to decrypt the necessary data.
It should be said, despite all the advantages of this encryption system, that the enterprise we are considering does not use it at all. This is connected both with the security policy itself, which does not provide for the most high level protection due to the lack of need for it. In addition, using EFS reduces the performance of any system, and for efficient work In an enterprise network, speed is also very important.
3. Maintaining user accounts.
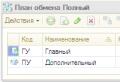
At the enterprise, each client using local network resources has a special account card (Appendix B). As you can see, it contains information about the user - name, password and network usage restrictions imposed on him.
Such cards allow you to classify (group) users who have similar resources into groups. As you know, groups will make it easier for the network administrator to provide access to certain resources. After all, it is enough to do only one action that gives permission to the entire group.
Control over online activities.
The Windows 2003 Server operating system installed on our enterprise server provides the system administrator with sufficient tools to control network activity, namely:
control the use of resources by the server;
check the data in the security log;
check entries in the event log;
provides the opportunity to see connected users online and the files they have open on their workstations;
warn the network administrator about certain errors.
User rights.
In our enterprise, user rights determine the types of actions allowed for him on the network.
The types of actions that are regulated by rights include logging on to the local computer, setting the time, shutting down, copying and restoring files from the server, and performing other tasks.
In a Windows 2003 Server domain, rights are granted and restricted at the domain level; If the group is directly in the domain, members have rights in all primary and backup domain controllers.
Each enterprise user must have their own access rights to information, permission to copy and restore files.
Monitoring sessions on workstations.
When a user, for example, coming to his office in the morning workplace, turns on the computer and starts a user session, asks for a username, password and domain, then the workstation sends the username and password to the domain for identification. In turn, the server checks the username and password in the domain user account database.
If the username and password are identical to the information on the account card, the server notifies the workstation that the session has begun. The server also loads other information when a user session begins, such as the user's settings, its directory, and environment variables.
By default, not all account cards in a domain allow you to log in. Only the Administrator, Server Operator, Print Control Operator, Account Card Management Operator, and Backup Control Operator group cards are allowed to do this.
Passwords and ID card policies.
Enterprises have all aspects of a password policy defined: a minimum password length (8 characters), a minimum and maximum password age, and password exclusivity, which prevents the user from changing their password to the password the user has recently used.
It is also possible to define other aspects of the registration card policy:
should the account card be blocked?
whether users should be forcibly disconnected from the server after the session start hours have passed;
whether users should be able to log in to change their password.
When account card locking is enabled, then the account card is locked after multiple unsuccessful attempts to start a user session, and no more than a certain period of time between any two unsuccessful attempts to start a session. Account cards that are blocked cannot be used to log in to the system.
If users are forcibly disconnected from servers when their session has timed out, then they receive a warning just before the end of the set session period. If users do not disconnect from the network, the server will force a disconnection.
In case the user is required to change the password, then if he has not done so with an expired password, he will not be able to change his password.
When a password has expired, the user must contact the system administrator for assistance in changing the password in order to be able to log into the network again.
If the user has not logged in and the time has come to change the password, he will be warned about the need to change as soon as he logs in.
As we found out, the built-in information protection measures on the part of the operating system are quite good and, if handled properly, can make a big contribution to ensuring the safety of information confidentiality and network performance.
Now we will try to consider software tools for protecting information on the network that are not directly related to the operating system.
First of all, let’s determine what information circulates in the network of NPO Mekhinstrument.
So, the network has:
1.information resources file server;
2.network shared resources (for example, printers); .database information resources; Such resources are divided into three corresponding groups, each of which has a number of resource names with an individual access level, location on the network, and individual code. It should be noted that at the enterprise we are considering, absolutely everything workstations where available important information, constituting a trade secret, for example, are equipped with additional software and hardware systems, the hardware of which forms the so-called “electronic lock”. In turn, it is a PCI board for electronic keys of such types as eToken, Smart Card, Proximity Card, Touch Memory. Such “electronic locks” have a number of functions: registering computer users and assigning them personal identifiers (names and/or electronic keys) and passwords to log into the system; requesting a user's personal ID and password when booting the computer. The request is carried out by the hardware before the OS loads; the ability to block the login of a registered user; maintaining a system log that records events related to system security; hardware protection against unauthorized loading of the operating system from a floppy disk, CD-DVD ROM or USB ports; monitoring the integrity of files on the hard drive; monitoring the integrity of physical sectors of the hard disk; opportunity collaboration with software to protect against unauthorized access. As indicated, our enterprise network has a connection to the World Wide Web. Control over the work of each employee on the World Wide Web is quite strict. Namely, the system administrator provides access for a specific workstation to the World Wide Web based on the log. Such access is available only for a certain time using special software. Therefore, users cannot simply use Internet resources; this is caused not only by security reasons, but also from the point of view of productivity of workers who can spend working time surfing the World Wide Web, not related to production purposes. Thus, the enterprise controls access to the Internet using the following methods: a log of access for each user is kept, which reflects the decision for which he is allowed to work on the Internet, the time of work and the maximum duration, the signature of the manager; A special log of work is also kept on the Internet, which indicates the user’s full name, date, time of start of work, duration of work, purpose of work, resources used, signature of the manager. Such measures are considered completely justified, especially if the real production needs for using the Internet are not very large and not frequent. Keeping such logs and records of used firewall software allows you to fairly well protect your network from malware that can come from infected sites or files downloaded from the Internet. At the enterprise we are considering, there is also the so-called “custodial protection” of data. A trustee is a user who has rights and privileges to access network file resources. Therefore, each employee has one of the eight existing types of rights: - the right to Read open files; - the right to Write to open files; - the right to Open an existing file; - the right to Create (and simultaneously open) new files; - the right to Delete existing files; - Parental rights: the right to Create, Rename, Erase directory subdirectories; the right to establish trustees and rights in the catalogue; the right to Establish trustees and rights in a subdirectory; - the right to Search a directory; - the right to Modify file attributes. To prevent accidental changes or deletions of individual files by all workers, file attribute protection is used. This protection applies to public information files that are typically read by many users. There are four file attributes used in data protection: write-read; read only; shared; undivided; It is also important that all workstations and the server are password protected. A password is set on the BIOS of each computer to prevent malicious software from changing the settings. In addition, each workstation with Windows XP SP3 installed is protected by a login password. The case of each computer is sealed with a holographic sticker to eliminate control over the physical reset of the PC. In my opinion, the most important and relevant at the enterprise we are considering is ensuring antivirus protection. After all, malicious software can cause enormous harm to the integrity and security of confidential data. There are also a sufficient number of ways through which malware can penetrate. Moreover, these paths are almost impossible for the administrator to control. Firstly, despite the fact that Internet access for users is limited, and each session of using the World Wide Web is strictly logged, there is still the possibility of becoming infected with a virus, for example, when viewing an infected site, receiving malware through instant messaging programs and email. Therefore, even during these limited Internet access sessions, the possibility of infection cannot be ruled out. In addition, it should be noted that currently any unscrupulous employee can connect his PC to the Internet using a USB 3G - EDGE modem, which are now very common and work wherever there is coverage cellular communications. In this case, any Internet resources can be visited. Secondly, employees may well bring with them and connect removable media without the administrator’s knowledge - USB Flash Drives or external portable hard drives, which may also contain malicious software. In addition, infection can also occur through CD DVD drives, which some workstations are equipped with. After all, employees can bring their own discs with unknown content. An attacker can also infect a network using removable media by entering the enterprise under any pretext. That is why ensuring the proper level of anti-virus security in an enterprise is an important issue. Of course, ensuring anti-virus security is a complex measure, but a very important role here is played by the choice of an anti-virus program, which must meet all modern requirements for application self-protection, efficiency, compatibility with the OS and other programs. In addition, the product must be at an optimal cost. Although, of course, you cannot skimp on safety. Let's look at antivirus products that are actively developing and are now widely distributed on the market. Let's give them a brief overview and comparison. Currently, an antivirus product called Doctor Web is becoming increasingly popular. Dr.Web 6.0 (“Doctor Web”). In English, the name of this program is translated as “healing web.” This antivirus is an exclusively domestic development, and has recently earned recognition from foreign experts. Dr.Web can be classified as a doctor detector; the antivirus detects viruses, removes them, “cures” infected files, is capable of monitoring network traffic, and checking email. In addition, this software product includes heuristic analyzer, which allows you to detect unknown threats using a special algorithm and combat them. This allows us to resist the self-modifying mutant viruses that are now widespread. We can say with confidence that this antivirus meets all modern requirements for such software and is able to compete with both foreign products and Kaspersky Lab products. During initial testing, you should not allow the program to disinfect files in which it detects a virus, since it cannot be ruled out that the sequence of bytes accepted as a pattern in the antivirus may occur in a healthy program. On at the moment, in my opinion and judging by latest reviews antivirus software experts, the leading position is occupied by the newest Kaspersky Lab product - Kaspersky Internet Security 2011, the latest available version of which at the time of writing this work is 11.0.2.256. Considering the positive reviews in many publications about the new Kaspersky Lab product, I would like to dwell on it in a little more detail. After all, according to many experts and analysts, Kaspersky Internet Security 2011 is capable of providing the most optimal level of protection against viruses, both known and unknown threats. In addition, a number of significant improvements are obvious compared to the 7th version of Kaspersky Anti-Virus. After the products Kaspersky Internet Security 2011 (KIS 2009) and Kaspersky Anti-Virus 2009 were released, several leading British IT publications published reviews where the efficiency, ease of use, high speed and low resource intensity of the new products were highly rated. In addition to the high level of protection, which we will look at a little later, new products provide high performance. After all, we have heard many complaints about the high consumption of system resources by products such as KIS 6.0 and even 8.0. Kaspersky Internet Security 2011 reduces resource consumption, which is especially noticeable compared to other modern antivirus programs. Thus, the operating system boot time from installed antivirus increased by only 1 second compared to an unprotected computer, and the Anti-Virus itself takes up only 20-odd megabytes of RAM, which is very little by the standards of modern anti-viruses. In addition, KIS 2011 takes up only about 100 megabytes of disk space (for comparison, other modern products take up several hundred megabytes!). It should be noted that the KIS 2011 interface is very beautiful and understandable (Appendix B). In addition to the fact that KIS 2011 consumes few system resources, we should not forget that this is not just an antivirus, but a whole complex for protecting your computer from viruses known by signatures and unknown, network attacks, phishing, and spam. KIS 2011 also has a built-in module for protecting the integrity and controlling applications, system registry, system files, boot sectors. Kaspersky Anti-Virus 2011 and KIS 2011 were developed taking into account their work on the new Windows 7 operating system (and the product supports both 64-bit and 32-bit versions of this OS). These products are also perfectly compatible with Windows XP. Thanks to the transition to a modern engine (“KLAVA”), KIS 2011 quickly searches for viruses in databases, the size of which has recently increased exponentially. New product works better with large compressed objects. KIS 2011 is now able to better process multiply packed objects, create “black” and “gray” lists of packed files, taking as a basis the applications that were used to compress them. Particularly noteworthy is the new KLAVA engine, which is optimized for working with multi-core processors, which are now widespread even in inexpensive computers. Thanks to this, the program can process data in several threads, and therefore much faster. The performance gain is especially great in 64-bit OS. The new Kaspersky Internet Security module helps protect against possible attacks that are carried out through vulnerabilities. After installing the product, it itself begins to analyze the system and installed programs. This usually takes 5-10 minutes. Kaspersky Internet Security displays a list in which you can see the name of the program and the severity of the unpatched vulnerability. In addition, for vulnerabilities found for each application, a link to the Viruslist.ru website is displayed, upon clicking on which you can get detailed information about the nature of vulnerability. There are also links to download updates that cover vulnerabilities. Thus, by using the Security Analysis function at least once a week and promptly eliminating vulnerabilities, you can be sure that all programs you work with are protected from external attacks. It should be noted that the price of these antivirus products is low. In addition to the antivirus tools discussed above, there are also a sufficient number of others, both paid and free (for example, Avast antivirus!). A complete list of them may simply be beyond the scope of this bachelor's work. Therefore, when choosing antivirus software, you need to base your choice on professional testing of antivirus products. Anti-Mailware company provides generalized data from testing antivirus products in 2011 on its website (#"justify">system-level protection (tested on the latest Windows 7 OS); protecting processes from termination; protection of processes from modification (a very important parameter); protection of drivers and system files. According to Anti-Mailware, the Russian antivirus KIS 2011, which was already discussed above, won only by a small margin over the product ZoneAlarm Internet Security Suite 2010. He was awarded the Platinum Medal by Anti-Mailware (Appendix D). Therefore, we can say that KIS 2011 is currently the most optimal anti-virus protection tool for the enterprise in question. Therefore, it is necessary to install it on each workstation. In this case, a fairly high level of anti-virus protection will be provided. Using the Internet, you can easily update signatures, which will keep your protection up to date. To summarize, we can say that the enterprise under study has organized a fairly high level of information protection, both physically and programmatically. The local network of this enterprise has almost all the features of a secure information system. Therefore, at the moment it is only necessary to support this protection in constant readiness to repel possible attacks by intruders. In the future, it is possible to update the software component of the server and workstations on Windows Server 2008 and Windows 7, respectively, as they meet more modern information security requirements. 2.4 Evaluating the effectiveness of an information security option If we talk about regulatory documents, the methods of functional standardization in the field of information security are set out in a separate international standard ISO/IEC 15408-99 “Criteria for assessing the security of information technologies.” But they are not entirely criteria for assessing safety in this standard; they are only a certain set of general technical requirements, standards that define, and the appearance of systems depending on their purpose, is quite vague. In our country, assessing the effectiveness of information protection must also take into account the special GOST R 50922-96. According to it, the assessment of the effectiveness of protection is also probabilistic in nature. An assessment of the effectiveness of information protection must necessarily take into account these objective circumstances, and its characteristics, as follows from GOST R 50922-96, must be probabilistic in nature, that is, assess probable threats to security and measures to prevent them. Statistics from the US FBI national agency, namely the High Technology Crime Branch, indicate that from 87 to 97% of all attacks on corporate networks of enterprises, organizations or institutions not only go unpunished, but are not even detected by security systems. All this suggests that very often attackers select non-standard way attack, completely new and unknown to anyone. That is why assessing possible risks and the degree of security is an extremely difficult task. Of course, in this case we're talking about about the high professionalism of attackers who carry out malicious actions. There is also a significant percentage of so-called unprofessional “hackers”, of which there are much more, as well as malware that will automatically spread throughout the World Wide Web. Therefore, network security tools must at least provide a minimum percentage of protection against common network threats that were described in this work. Regulatory documents on assessing IT security practically do not contain specific methods, as a result of which the gap between general declarations and specific tools for implementing and monitoring their provisions is unacceptable. To assess the likelihood of threats to the network and their degree, it is necessary to conduct special research using special methods that are simply impossible to carry out due to the limitations of the bachelor’s final qualifying work. However, the degree and effectiveness of network security can be assessed by the regulatory criterion of the components of the enterprise network protection system. They are presented in Figure 1. Thus, an information protection system can only be complete if there is: Legislative, regulatory and scientific framework; Bodies (divisions) ensuring IT security; Organizational, technical and regime measures, as well as methods (information security policy); Software and hardware methods and means. Figure 1 - main parts of protection Based on the results of this study, we can confidently say that each of the listed points is present in the protection system of the enterprise in question. The implementation of these points is organized depending on the capabilities and potential of the enterprise in order to ensure the maximum level of protection based on the available funds. Therefore, we can say that the effectiveness of protection is not at the maximum, but at a level quite high for the specifics of the enterprise. In principle, an absolutely protected IP cannot exist; there is always the possibility of certain threats; the question of protection is only in minimizing this probability as much as possible. Conclusion
Let us draw general conclusions based on the research conducted in this final qualification work. In the current problem of information security in networks, which is becoming increasingly relevant, as the results of our research showed, we have identified three main aspects of vulnerability: the danger of unauthorized access to information by persons for whom it is not intended; the possibility of distortion or destruction of confidential, valuable information; the possibility of modifying information, both accidental and intentional. Ensuring the protection of information is now becoming, as it has been found out, the most important condition for the normal functioning of any information system. This is especially true in business and government agencies, where information can be very valuable and therefore requires enhanced protection from intruders. In information protection, three main and complementary areas can now be distinguished: continuous improvement of technologies and organizational and technical measures of information processing technology in order to protect it from external and internal security threats; blocking unauthorized access to information using special technical means. However, there are also factors that make it difficult to solve this currently difficult problem - information security in networks. The main factors - obstacles are: massive use of information technologies; the increasing complexity of IS functioning; constant increase in the number of threats and epidemics of computer viruses. As for the constantly growing number of threats to information security, as we found out in the course of our work, we can identify a number of their main threats: leak of confidential information; compromise of information; refusal of information; unauthorized exchange of information between subscribers; unauthorized use of information resources; violation of information services; erroneous use of information resources; illegal use of user and administrator privileges. Ensuring information security is the application of a whole range of measures aimed at protecting against security threats. The development and application of such measures (both preventive and to repel real attacks and threats) should be based on certain fundamental principles of protecting information on the network. When building an IS security system, there must be a systematic approach (the principle of a systems approach), which means the optimal combination of interrelated organizational hardware, software, physical and other properties. The security system must constantly evolve to take into account new trends in the development of security systems, security methods and new security threats. This constitutes the principle of continuous development of the NIB. Constant monitoring and recording of unauthorized access attempts is required. A certain level of security system reliability must be ensured at all times. With the recent development of malware, it is important to consider the principle of providing all possible anti-virus tools. The construction of effective anti-virus protection, the use of anti-virus programs and means of quickly restoring system functionality after a virus attack should be ensured by an information security system. In practice, we examined the network of a specific enterprise - NPO Mekhinstrument LLC, where we studied all the methods and means of information security used on it. During the study of the network security system, it was found that anti-virus protection has now acquired special importance. My recommendations are that you must use the latest anti-virus protection tools. It is important now to use multi-level anti-virus protection and use a suite of anti-virus software. The review of anti-virus programs carried out in the work showed a high assessment of the product from Kaspersky Lab KIS 2011. In my opinion, it is now the most optimal means of protection not only against viruses, but also against a number of other threats to information security. I also recommend online backup. Place your data in one of the modern cloud services, such as Dropbox (www.dropbox.com) or Gigabank (www.gigabank.de/en), and you will be protected from data loss. You can recover your files even if a criminal stole your computer along with all its hard drives or your house burned down. Thus, to ensure security in an information system or network, a system administrator or a special security service must take into account not only the basic principles of information security, but also adopt constantly improving methods and methods of protection. Taking into account many parameters of the protected network, the characteristics of the organization, the nature of its activities and budget, a specific information security policy must be created. It is constantly necessary to take into account new threats and update software and hardware security systems. For a specific enterprise network, it is proposed to introduce an information encryption system and update the software of workstations and servers using more modern Windows 2008 server and Windows 7 operating systems. Therefore, building a competent methodology for ensuring information security in each specific case, taking into account all internal and external factors, will make it possible to create a truly effective information security system, providing a sufficient level of protection. List of sources used
.Bezrukov, N.N. Computer viruses [Text] / N.N. Bezrukov. - M.: Nauka, 2011.- 345 pp.- ISBN 978-5-0395-2489-243 .Kirsanov, D. A. Clear Internet. [Text] - M.: Symbol-Plus, 2011. - 198 p. - ISBN 978-5-0245-13590-4124-1 .Melnikov, V. A. Information protection in computer systems Oh. [Text] - M.: Finance and Statistics, 2011. - 268 p. - ISBN 978-5-79469-3458-231 .Simonovich, S. V. et al. Computer science: Basic course. [Text] - St. Petersburg: Peter, 2011. - 455 p. - ISBN 978-5-56504-2140-5344-124640 .Titorenko, G.A. Management information technologies. [Text] - M.: Unity, 2011. - 411 pp. - ISBN 978-5-190241-14125-23-43265 .Criminal Code of the Russian Federation dated June 13, 1996 No. 63-FZ as amended. 03/07/2011 // Legal reference system “Consultant Plus”: [Electronic resource] / Company “Consultant Plus”. - Last. Update 03/06/2012. .Stepanov, V. With a computer on your own. [Text] - M.: Unity, 2010. - 368 p. - ISBN 978-5-243-5435-143 .Gaikovich, V.Yu., Pershin, A.Yu. Security of electronic banking systems. [Text] \ V.Yu. Gaikovich - M.: United Europe, 2010. - 458 p. ISBN 210-2325-246500048-311 .Maksimenkov, A.V., Seleznev, M.L. Fundamentals of designing information-computing systems and computer networks. [Text] - M.: Radio and communication, 2010. - 398 p. - ISBN 978-5-221-2359-131-001 .Mostovoy, D.Yu. Modern technologies for fighting viruses [Text] // PC World. No. 4. 2010. - 104 p. .Nechaev, V. I. Elements of cryptography. [Text] Fundamentals of the theory of information security. M. 2010. - 359 p. - ISBN 978-5-49-12540-2680 .Severin, V.A. Comprehensive information protection in the enterprise. [Text] Grief UMO RF Ministry of Defense. - M.: Gorodets, 2010. - 387 p. ISBN 978-5-21049-462342-1425 .Khomonenko, A. D. Fundamentals of modern computer technologies. [Text] Textbook for Universities. - St. Petersburg: Crown print, 2010. - 412 p. - ISBN 978-5-8240-12845-1241-345 .Yakimenko, A.S. Information security tools. [Text] - M.: Unity, 2010. - 238 p. - ISBN 978-5-9102-4801-48 .Kirk, Cheryl. Internet. Book of answers. [Text] - M.: Unity, 2009. - 220 p. - ISBN 978-5-7832-14150-231 .Kornyshev, Yu.N., Romantsov, V.M., Stovbun, G.V. Alarm on telephone networks: Textbook. Manual [Text] / Ukrainian State Academy of Communications named after. A.S.Popova. Odessa, 2009. - 420 p. ISBN 978-5-221-23029-2420881 .Kupriyanova, G. I. Information resources Internet. [Text] - M.: EDEL, 2009. - 209 p. ISBN 978-5-364-643523-4352 .Levin, V. K. Self-instruction manual for useful programs. 3rd of. [Text] - St. Petersburg: Peter, 2009. - 377 p. ISBN 978-5-245-3250-12453-11 .Beluntsov, V.O. PC hardware. 8th edition. [Text] - M.: TechBook, 2009. - 98 p. - ISBN 978-5-223-43259-493 .Brown, S. Mosaic and World Wide Web for Internet access: Per. from English [Text] - M.: Mir: Malip: SK Press, 2009. - 234 p. - ISBN 978-5-1435-2326-01482 .Levin, V.K. Information protection in information computing systems and networks [Text] // Programming. N3. 2009. - 90 p. - ISBN 978-5-41-1243-11 .Goldstein, B.S. Switching systems: Textbook for universities. 2nd ed. [Text] - St. Petersburg: BHV - St. Petersburg, 2009. - 385 p. ISBN - 978-5-12501-450-124-432 .Goncharok, M. Kh., Kryukov, Yu. S. Construction of an information security system in digital telephone exchanges and selection of a security class // Information Protection. Confidential. [Text] - 2009. No. 2. - 56 pp. - ISBN 978-5-2145-1425-63 .Makarova, N.V. Computer Science: Textbook. [Text] - M.: Finance and Statistics, 2009. - 245 p. - ISBN 978-5-492184-2830-22-4590 .Federal Law of February 20, 1995 N 24-FZ “On information, informatization and information protection.” in the last ed. Federal laws from 03.25.2009 / Legal reference system “Consultant-plus.” [Electronic resource]/ Company “Consultant-plus.”/ Last. Update 03/06/2012. .Melnikov V.P., Kleimenov S.A., Petrakov A.M. Information security and information protection. [Text] Study guide. M. Academy. 2009. - 589 p. - ISBN 978-5--41295-4123467-433 .Nazarova, S. V., Local computer networks. [Text] M.: Finance and Statistics, 2008. Nemeth E., Snyder G., Seabass S., Hein T.R UNIX: a guide system administrator: Per. from English - K.: BHV, 2009. - 490 p. ISBN 978-5-3590-234 .Pravikov, D. I. Key floppy disks. Development of elements of systems to protect against unauthorized copying. [Text] - M.: Radio and Communications, 2009. - 289 p. - ISBN 978-5-8945-31480 .Rachkov, V. A. et al. Computer for students. Self-instruction manual. 3rd edition. [Text] - St. Petersburg: Peter, 2009. - 256 p. - ISBN 978-5-9243-4091-212 .Walker, V., Blake, Y. Computer security and organization of their protection. [Text] - M.: Finance and Statistics, 2009. - 344 p. - ISBN 978-5-9839-32470-1234-1 .Ferrari D. Assessing the performance of computing systems. [Text] - St. Petersburg: Peter, 2009. - 495 p. - ISBN 978-5-283-1252305-4845031-138 .Hofman, L. Modern methods of information security. [Text] St. Petersburg: Peter, 2009. - 329 p. - ISBN 978-5-4920-329049-2329-001 .Schneier, Bruce, Applied Cryptography. Protocols, algorithms, source texts in S. [Text] - M.: TRIUMPH Publishing House, 2009. - 540 p. - ISBN 978-5-82048-4895048-4890-59033 .Kaspersky, E. Computer viruses. [Text] M.: EDEL Publishing House, 2008. - 257 p. ISBN 978-5-78924-4242-4128-2 .Kent, Peter. Internet / Radio and communications. [Text] - 2008. No. 8. - 89 p. - ISBN 978-5-1028-510823-325658-2 .Kuznetsov, A.A. Protection of business information (security secrets). [Text] M. Exam. 2008. - 155 p. ISBN 978-5-0491-41985460421 .Honeycart, Jerry Internet no problem. [Text] - M.: Radio and Communications, 2008. - 240 p. - ISBN 978-5-9351-5494-2491 .Shangin Vladimir Protection of computer information. Effective methods and means. [Text] M.: DMK-Press. 2008. - 239 p. - ISBN 978-5-5149-3155-544 .Decree of the Government of the Russian Federation of February 28, 1996 N 226 “On state accounting and registration of databases and data banks.” Legal reference system "Consultant-plus." [Electronic resource] / Consultant-plus company / Last. Update 03/06/2012.Similar works to - Methods and means of protecting information in networks
Data protection in computer networks is becoming one of the most pressing problems in modern computer science. To date, three basic principles of information security have been formulated, which should ensure:
Data integrity - protection against failures leading to loss of information, as well as unauthorized creation or destruction of data;
Confidentiality of information and, at the same time,
It should also be noted that certain areas of activity (banking and financial institutions, information networks, public administration systems, defense and special structures) require special data security measures and place increased demands on the reliability of the functioning of information systems.
When considering problems of data protection on the network, the first question that arises is the classification of failures and access violations that can lead to the destruction or unwanted modification of data. Among these potential “threats” are:
1. Hardware failures:
Cable system failures;
Power outages;
Crashes disk systems;
Failures of data archiving systems;
Failures of servers, workstations, network cards etc.;
2. Loss of information due to incorrect operation of the software:
Loss or change of data due to software errors;
Losses when the system is infected with computer viruses;
3. Losses associated with unauthorized access:
Unauthorized copying, destruction or falsification of information;
Familiarization with confidential information constituting a secret of unauthorized persons;
4. Information loss associated with improper storage of archival data.
5. Errors of service personnel and users.
Accidental destruction or modification of data;
Incorrect use of software and hardware, leading to the destruction or modification of data.
Depending on the possible types of network disruptions, numerous types of information protection are combined into three main classes:
Physical protection means, including protection means for the cable system, power supply systems, archiving means, disk arrays, etc.
Security software, including: antivirus programs, authority delimitation systems, access control software.
Administrative protection measures, including control of access to premises, development of a company security strategy, emergency action plans, etc.
It should be noted that such a division is quite arbitrary, since modern technologies are developing towards a combination of software and hardware protection.
Archiving and duplication systems
Organizing a reliable and efficient data archiving system is one of the most important tasks in ensuring the safety of information on the network. In small networks where one or two servers are installed, the most common method is to install an archiving system directly into the free slots of the servers. In large corporate networks, it is most preferable to organize a dedicated specialized archiving server.
Such a server automatically archives information from hard drives servers and workstations at the time specified by the administrator of the local computer network, issuing a report on the backup performed. This provides control of the entire archiving process from the administrator console, for example, you can specify specific volumes, directories or individual files that need to be archived.
It is also possible to organize automatic archiving upon the occurrence of an event (“event driven backup”), for example, when receiving information that there is little left on the hard drive of a server or workstation free space, or when one of the “mirror” disks on the file server fails.
To ensure data recovery in case of failures of magnetic disks, systems have recently been most often used disk arrays- groups of disks operating as a single device, complying with the RAID (Redundant Arrays of Inexpensive Disks) standard.
Protection against computer viruses
Today, in addition to the thousands of already known viruses, 100-150 new strains appear every month. The most common methods of virus protection to this day remain various antivirus programs.
However, in recent years, a combination of software and hardware protection methods has increasingly been used as a promising approach to protection against computer viruses. Among the hardware devices of this type are special anti-virus boards that are inserted into standard computer expansion slots.
Protection against unauthorized access
The problem of protecting information from unauthorized access has become especially acute with the widespread use of local and, especially, global computer networks. It should also be noted that often the damage is caused not because of “malicious intent”, but because of simple user errors who accidentally damage or delete vital data. In this regard, in addition to access control, a necessary element of information protection in computer networks is the delimitation of user powers.
In computer networks, when organizing access control and delimiting user powers, built-in tools of network operating systems are most often used
There are many possible directions of information leakage and ways of unauthorized access in systems and networks. Among them:
reading residual information in system memory after executing authorized requests;
· copying storage media and information files by overcoming security measures;
· disguise as a registered user;
· disguise as a system request;
· use of software traps;
· exploitation of operating system deficiencies;
· illegal connection to equipment and communication lines;
· malicious disabling of protection mechanisms;
· introduction and use of computer viruses.
Ensuring information security is achieved through a set of organizational, organizational, technical, technical and program measures.
To organizational measures information protection include:
· restriction of access to premises where information is prepared and processed;
· permission to process and transmit confidential information only to verified officials;
· storage of magnetic media and log books in safes closed to unauthorized persons;
· preventing unauthorized persons from viewing the contents of processed materials through a display, printer, etc.;
· use of cryptographic codes when transmitting valuable information over communication channels;
· destruction of ink ribbons, paper and other materials containing fragments of valuable information.
Organizational and technical measures information protection include:
· supplying power to equipment that processes valuable information from an independent power source or through special network filters;
· installation of combination locks on the doors of premises;
· use for displaying information during input-output of liquid crystal or plasma displays, and for obtaining hard copies - inkjet printers and thermal printers, since the display produces such high-frequency electromagnetic radiation that the image from its screen can be received at a distance of several hundred kilometers;
· destruction of information when writing off or sending a computer for repair;
· installation of keyboards and printers on soft pads in order to reduce the possibility of reading information acoustically;
· limiting electromagnetic radiation by shielding rooms where information processing occurs with sheets of metal or special plastic.
Technical means Information security is a system for protecting territories and premises by shielding computer rooms and organizing access control systems. Protecting information on networks and computing facilities using technical means, it is implemented based on organizing access to memory using:
· control access to various levels of computer memory;
· data blocking and key entry;
· allocation of control bits for records for identification purposes, etc.
Software architecture information protection includes:
· security control, including control of login registration, recording in the system log, control of user actions;
· reaction (including audio) to a violation of the security control system for access to network resources;
· control of access credentials;
· formal control of the security of operating systems (basic system-wide and network);
· control of protection algorithms;
· checking and confirming the correct functioning of hardware and software.
To reliably protect information and identify cases of unauthorized actions, the operation of the system is recorded: special diaries and protocols are created in which all actions related to the protection of information in the system are recorded. Special programs are also used to test the security system. Periodically or at randomly selected points in time, they check the functionality of hardware and software protection measures.
A separate group of measures to ensure the safety of information and identify unauthorized requests includes real-time violation detection programs. Programs in this group generate a special signal when registering actions that may lead to illegal actions in relation to protected information. The signal may contain information about the nature of the violation, the location of its occurrence and other characteristics. In addition, programs can deny access to protected information or simulate an operating mode (for example, instant loading of input/output devices) that will allow the intruder to be identified and detained by the appropriate service.
One of the common methods of protection is an explicit indication of the secrecy of the output information. This requirement is implemented using appropriate software.
By equipping a server or network workstations, for example, with a smart card reader and special software, you can significantly increase the level of protection against unauthorized access. In this case, to access the computer, the user must insert a smart card into the reader and enter his personal code.
Smart access control cards allow you to implement, in particular, functions such as entry control, access to devices personal computer, access to programs, files and commands.
Bridges and remote access routers use packet segmentation - dividing them and transmitting them in parallel over two lines - which makes it impossible to “intercept” data when a “hacker” illegally connects to one of the lines. In addition, the compression procedure of transmitted packets used during data transmission guarantees the impossibility of decrypting the “intercepted” data. In addition, remote access bridges and routers can be programmed to restrict remote users from accessing certain resources on the main office network.
Security Mechanisms
1. Cryptography.
To ensure secrecy, encryption, or cryptography, is used, which allows you to transform data into an encrypted form, from which the original information can only be extracted if you have a key.
Encryption is based on two basic concepts: algorithm and key. An algorithm is a way to encode source text, resulting in an encrypted message. An encrypted message can only be interpreted using the key.
All elements of protection systems are divided into two categories - long-term and easily replaceable. Long-term elements include those elements that relate to the development of security systems and require the intervention of specialists or developers to change. Easily replaceable elements include system elements that are intended for arbitrary modification or modification according to a predetermined rule, based on randomly selected initial parameters. Easily replaceable elements include, for example, a key, password, identification, etc.
The secrecy of information is ensured by introducing special keys (codes) into the algorithms. Using a key in encryption provides two significant advantages. Firstly, you can use the same algorithm with different keys to send messages to different recipients. Secondly, if the secrecy of the key is compromised, it can be easily replaced without changing the encryption algorithm. Thus, the security of encryption systems depends on the secrecy of the key used, and not on the secrecy of the encryption algorithm.
It is important to note that increasing technology productivity leads to a decrease in the time required to open keys, and security systems have to use increasingly longer keys, which, in turn, leads to increased encryption costs.
Since such an important place in encryption systems is given to key secrecy, the main problem of such systems is the generation and transmission of the key.
There are two main encryption schemes: symmetric encryption (also sometimes called traditional or private key encryption) and public key encryption (sometimes called asymmetric encryption).
With symmetric encryption, the sender and recipient own the same key (secret) with which they can encrypt and decrypt data.
Electronic signature
Using an electronic signature, the recipient can verify that the message he received was sent not by a third party, but by a sender with certain rights. Electronic signatures are created by encrypting the checksum and additional information using private key sender. Thus, anyone can decrypt the signature using the public key, but only the owner of the private key can create the signature correctly. To protect against interception and reuse, the signature includes a unique number - a sequence number.
Authentication
Authentication is one of the most important components of organizing information security on the network. Before a user is granted the right to obtain a particular resource, it is necessary to ensure that he is really who he claims to be.
When a request is received to use a resource on behalf of a user, the server providing the resource transfers control to the authentication server. After receiving a positive response from the authentication server, the user is provided with the requested resource.
When authenticating, as a rule, the principle is used, called “what he knows” - the user knows some secret word, which he sends to the authentication server in response to his request. One authentication scheme is the use of standard passwords. Password - entered by him at the beginning of a session of interaction with the network, and sometimes at the end of the session (in especially critical cases, the password for normal exit from the network may differ from the input one). This scheme is the most vulnerable from a security point of view - the password can be intercepted and used by another person.
The most commonly used schemes are one-time passwords. Even if intercepted, this password will be useless the next time you register, and obtaining the next password from the previous one is an extremely difficult task. To generate one-time passwords, both software and hardware generators are used, which are devices inserted into a computer slot. Knowledge of the secret word is necessary for the user to operate this device.
Network protection
Recently, corporate networks are increasingly being connected to the Internet or even using it as their basis. Firewalls are used to protect corporate information networks. Firewalls are a system or combination of systems that allow you to divide a network into two or more parts and implement a set of rules that determine the conditions under which packets can pass from one part to another. As a rule, this boundary is drawn between the enterprise local network and INTERNETOM, although it can also be drawn internally. However, it is not profitable to protect individual computers, so the entire network is usually protected. The firewall passes all traffic through itself and for each passing packet it makes a decision whether to let it through or discard it. In order for the firewall to make these decisions, a set of rules is defined for it.
The firewall can be implemented either in hardware (that is, as a separate physical device) or in the form special program running on the computer.
Typically, changes are made to the operating system that the firewall is running on to make the firewall itself more secure. These changes affect both the OS kernel and the corresponding configuration files. The firewall itself is not allowed to have user sections, and therefore no potential holes - only an administrator section.
Some firewalls only work in single-user mode, and many have a system for checking the integrity of program codes.
A firewall typically consists of several different components, including filters or screens that block some traffic from passing through.
All firewalls can be divided into two types:
· packet filters, which filter IP packets using filtering routers;
· application level servers that block access to certain services on the network.
Thus, a firewall can be defined as a set of components or a system that sits between two networks and has the following properties:
· all traffic from the internal network to the external network and from the external network to the internal network must pass through this system;
· only traffic defined by the local security strategy can pass through this system;
Information security software. Specialized software tools for protecting information from unauthorized access generally have better capabilities and characteristics than built-in network OS tools. In addition to encryption programs, there are many other external information security tools available. Of the most frequently mentioned, the following two systems should be noted that allow limiting information flows.
Firewalls - firewalls (literally firewall - fire wall). Special intermediate servers are created between the local and global networks, which inspect and filter all network/transport level traffic passing through them. This allows you to dramatically reduce the threat of unauthorized access from outside to corporate networks, but does not eliminate this danger completely. A more secure version of the method is the masquerading method, when all traffic originating from the local network is sent on behalf of the firewall server, making the local network practically invisible.
Proxy-servers (proxy - power of attorney, trusted person). All network/transport layer traffic between the local and global networks is completely prohibited - there is simply no routing as such, and calls from the local network to the global network occur through special intermediary servers. It is obvious that with this method, access from the global network to the local one becomes impossible in principle.
VPN (virtual private network) allows you to transmit secret information through networks in which it is possible for unauthorized people to eavesdrop on traffic. Technologies used:
PPTP (a point-to-point tunneling protocol that allows a computer to establish a secure connection with a server by creating a special tunnel in a standard, unsecured network. PPTP places (encapsulates) PPP frames in IP packets for transmission over a global IP network, such as the Internet. ),
PPPoE ( network protocol transmission of PPP frames over Ethernet. Mainly used by xDSL services. Provides additional capabilities (authentication, data compression, encryption), IPSec (a set of protocols to ensure the protection of data transmitted over the Internet Protocol, allows authentication and/or encryption of IP packets. IPsec also includes protocols for secure key exchange in Internet.)
Hardware information security.
Hardware protection includes various electronic, electronic-mechanical, and electro-optical devices. To date, a significant number of hardware devices for various purposes have been developed, but the most widespread are the following:
special registers for storing security details: passwords, identification codes, classifications or security levels;
devices for measuring individual characteristics of a person (voice, fingerprints) for the purpose of identification;
circuits for interrupting the transmission of information on a communication line for the purpose of periodically checking the data output address.
devices for encrypting information (cryptographic methods).
Protection against malware.
Currently, one of the main issues of information security is protection against malware. There are a huge number of types of malware: viruses, Trojan horses, network worms, logic bombs - and every day there are more and more of them. Protection against malware is not limited to the traditional installation of antivirus tools on user workstations. This is a complex task that requires an integrated approach to solution. One of the main advantages of this solution is that the information protection subsystem against malware is considered as a multi-level system.
The first level includes anti-malware protection tools installed at the interface with global networks (Internet gateway and/or firewall; public servers Web, SMTP, ftp.) and filtering the main types of traffic (HTTP, SMTP, FTP, etc.)
The second level is protection tools installed on internal corporate servers and workgroup servers (file storage, application servers, etc.).
And finally, the third level is anti-malware protection installed on user workstations, including remote and mobile users.
The advantages of this solution are:
- - using products from world leaders;
- - centralized management of the entire anti-malware subsystem;
- - V automatic update antivirus databases;
- - in close interaction of anti-virus tools at all levels of the subsystem, etc.
Protection against computer viruses.
Antivirus programs have been and remain the main means of fighting viruses. You can use antivirus programs (antiviruses) without having any idea how they work. However, without understanding the principles of antivirus software, knowing the types of viruses, as well as how they spread, it is impossible to organize reliable computer protection. As a result, the computer may be infected even if antivirus software is installed on it.
Today, several fundamental techniques for detecting and protecting against viruses are used:
- - scanning;
- - heuristic analysis;
- - use of anti-virus monitors;
- - change detection;
- - use of antiviruses built into the computer BIOS.
In addition, almost all antivirus programs provide automatic recovery infected programs and boot sectors. Of course, if possible.
Features of corporate intranet protection.
A corporate intranet can consist of hundreds or thousands of computers that act as workstations and servers. This network is usually connected to the Internet and contains mail servers, document automation system servers such as Microsoft Exchange and Lotus Notes, and non-standard information systems.
To reliably protect a corporate intranet, it is necessary to install antivirus software on all workstations and servers. At the same time, on file servers, servers email and servers of document management systems, special server anti-virus software should be used. As for workstations, they can be protected with conventional anti-virus scanners and monitors.
Special anti-virus proxy servers and firewalls have been developed that scan traffic passing through them and remove malicious software components from it. These antiviruses are often used to protect mail servers and document management system servers.
Protecting mail servers.
Antivirus monitors are ineffective at detecting viruses in mail messages. This requires special antiviruses that can filter SMTP, POP3 and IMAP traffic, preventing infected messages from reaching user workstations.
To protect mail servers, you can purchase antiviruses specifically designed to scan mail traffic, or connect regular antiviruses that can operate in command line mode to your mail server.
Protection of non-standard information systems.
For anti-virus protection of non-standard information systems that store data in their own formats, it is necessary to either build an anti-virus kernel into the system or connect an external scanner operating in command line mode.
Submitting your good work to the knowledge base is easy. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Similar documents
Information security regime formation system. Problems of information security of society. Information security tools: basic methods and systems. Protection of information in computer networks. Provisions of the most important legislative acts of Russia.
abstract, added 01/20/2014
Level of development of information technology. Dependence of the security of the Russian Federation on ensuring information security. Characteristics of Internet begging. Fraud related to online stores. Types of computer viruses.
presentation, added 04/06/2015
Features and principles of software security. Reasons for creating viruses to infect computer programs. General characteristics computer viruses and means of neutralizing them. Classification of methods of protection against computer viruses.
abstract, added 05/08/2012
Studying the concept of a corporate information system; requirements for their development. Familiarization with the process of designing and implementing these computer technologies in production. Consideration of the specifics of the operation of corporate information systems.
course work, added 11/02/2014
Information protection and its types. The role of information security. Protection against unauthorized access to information. Physical protection of data on disks. Types of computer viruses. Protection against malware and spam (antiviruses, hacking utilities).
presentation, added 10/04/2014
Development of an information system to improve the efficiency of car service management through the use of modern computer technologies. Building a database in Microsoft SQL Server. Description of the user interface.
thesis, added 01/27/2009
Objectives, structure, physical, software and hardware measures to protect the information system. Types and causes of computer crimes, ways to improve an organization's security policy. Purpose and main functions of the "Diary" folder in MS Outlook 97.
test, added 04/01/2009
Methods and means of protecting information data. Protection against unauthorized access to information. Features of protecting computer systems using cryptography methods. Criteria for assessing the security of information and computer technologies in European countries.
test, added 08/06/2010